Despite ever-improving junk mail filters and more sophisticated defense measures, phishing is still one of the biggest threats to cyber security and they’re becoming increasingly difficult to recognize. Criminals are using Large Language Models (LLMs) such as ChatGPT to formulate their emails, which results in largely error-free texts with correct grammar and understandable sentence structure.
As hackers become more advanced, you’ll need to learn new methods to detect them and stay one step ahead of the game. Below we’ll share a few ways you can catch them in the act, and hopefully avoid falling prey to their scams.
Further reading: Top 9 phishing scams to watch out for in 2024
Phishing from AI accounts
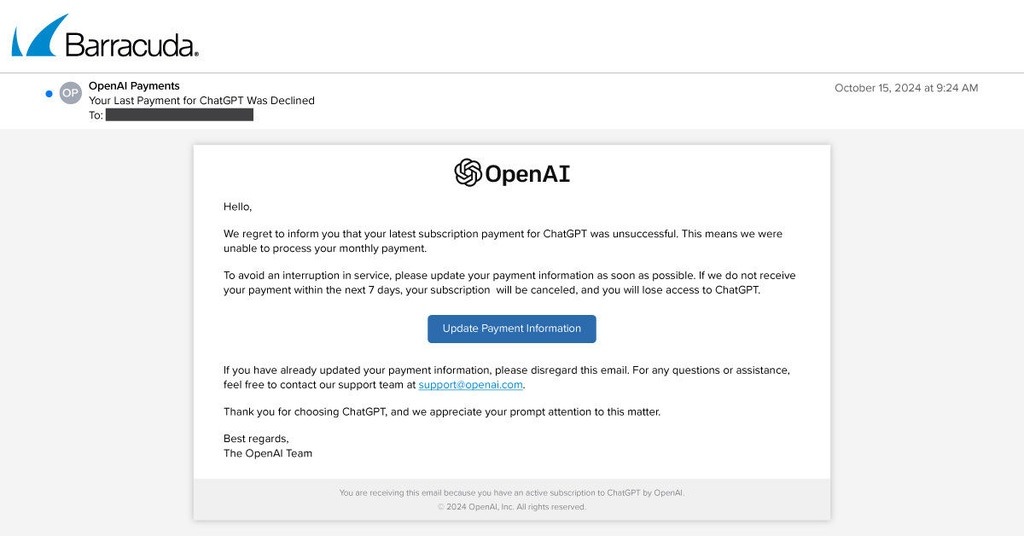
Barracuda Networks draws attention to new phishing emails that attempt to steal access to the paid ChatGPT accounts. These are currently in high demand.
IDG
AI services such as ChatGPT or Google Gemini are becoming increasingly important for companies as they enable them to reduce their costs for routine correspondence or invoicing. Open AI, the manufacturer of ChatGPT, and Google therefore charge money for use once a certain number of queries have been made.
The security company Barracuda Networks has now reported that an extensive phishing campaign has been launched in an attempt to steal access to paid ChatGPT accounts.
The criminals are sending emails purporting to come from Open AI. In their emails, they explain that they are unable to debit the monthly payment. The recipient should now update their account information within seven days otherwise they will lose access to ChatGPT.
A button in the email leads to an online form for entering the account details. Such data can be easily sold via dark channels on the internet.
Streaming accounts
Fraudsters often try to steal login details for streaming services such as Netflix or Disney. In recent months, there have been several waves of phishing emails requesting data from Netflix accounts. Such accounts are particularly easy to monetize and are therefore popular with criminals.
Users receive an email purporting to be from a streaming service asking them to update their payment details. Otherwise, their account will be blocked in a few days. In the email, they see a button or a link that supposedly leads to their account. On the associated website, a form is waiting for them to enter their access data.
The email comes from a fraudster, which in most cases can be recognized just by looking at the sender’s address. Only a few phishing senders go to the trouble of forging the email address (the technical term for this is “spoofing.”)
You can easily find out where the button or link in the email, which supposedly leads to a form from the streaming provider, actually links to by pointing at it with the mouse for a second or two.
Typical for these and other phishing emails is that they’re urgent. Victims usually only have two or three days to resolve the problem. Or the perpetrators claim that the account has already been blocked and the email recipient must act quickly to reactivate it. In this way, the perpetrators build up time pressure so that their victims don’t think twice.
Smishing is becoming a plague
When a phishing attempt is sent via text message, it’s called smishing. New waves of smishing have been using the grandchild trick. In this case, the text reads: “Hi Dad, this is my new number. Can you write to me on WhatsApp?”
If the recipient actually makes contact, they’ll usually receive a reply about an accident or other emergency. To “help” whoever it is on the other end, the recipient will need to transfer a large sum to a specific account.
Password manager
Access to the encrypted vaults of password managers is particularly valuable to criminals.
If they succeed in tapping into the master password, they have free access to login data of all kinds, from bank accounts to online senders and streaming services to accounts with email services and telephone providers.
Fraudsters try to access the master password for the password manager LastPass. This would give them free access to all stored passwords and access data.
IDG
In spring 2024, a new approach by criminals became known.
They’re working with phishing kits that make it very easy to forge login forms on websites and add logos of the supposed owner companies. These kits are distributed online by criminal groups as part of phishing-as-a-service offers.
In the specific case, the login page of the password manager LastPass was recreated using such a kit. The attackers then started an automated series of calls in which a recorded message explained that a new device was trying to access the LastPass account.
The caller was told to authorize access by pressing “1” or block it by pressing “2.” If they dialed “2,” you’ll get a call from an alleged customer service employee.
The call comes from a real person who asks for the email address and then they’ll send the victim an email with instructions on how to reset the master password.
This email links to the criminal’s website, where the customer was asked to enter their previous master password. As soon as the criminals are in possession of this password, they log into LastPass and change the owner’s telephone number and email address so they no longer have access.
As the first contact between the fraudster and their victim is by telephone, this method is known as vishing or voice phishing.
Here, too, the criminals push the pace so that the people they call don’t have time to think. As password managers often store numerous access data for important accounts, it’s advisable to secure them with two-factor authentication or set up a login with a passkey.
PayPal and Klarna
The topic of data protection has now reached the general public. Many people know that there are legal regulations for companies on how they must handle their customers’ data. Criminals are taking advantage of this.
In an email with the logo of the payment service provider PayPal, they claim that the account has been blocked because the account information has not yet been confirmed.
To unblock the account, the customer would have to activate the “3DS Double Authorization.” Although 3DS authentication does indeed exist, PayPal calls it 3D Secure.
After clicking on the button, the recipient of the email is asked to enter their telephone number and PayPal login details. The fraudsters can then call back to request the missing data for the transfer and redirect payments to their account.
How to reliably recognize phishing emails
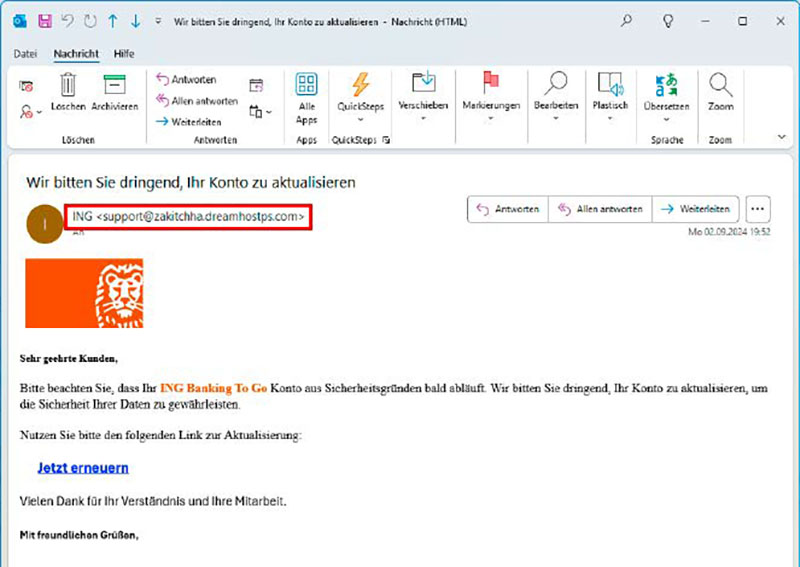
An email from ING Bank should also have an address with the domain extension ing.de and not come from support@zakitchha.dreamhostps.com. This is a clear indication that it is phishing.
IDG
Phishing can result in high financial losses, so be careful and take a close look at incoming emails:
- Phishing messages may be better worded these days thanks to AI, but they are still not error-free. You should be suspicious of foreign-language phrases, an incorrect or missing salutation, and an unusual choice of words.
- It’s typical of phishing attempts that the perpetrators put their victims under time pressure. They are asked to make a payment or provide personal details within a few hours or days, otherwise they face the threat of massive financial loss, arrest, or similar. The less time the sender gives you, the higher the probability that it’s a phishing e-mail.
- If the email contains a button or a link, point to it with the mouse (do not click!) and read the address to which it leads. If it’s not the page of the alleged sender company, you’re probably dealing with a phishing message.
- Enter the subject line of a suspicious email into Google and see if other people have received the same message.
If you suspect a phishing message, you should delete the email immediately and never respond to it.
This article originally appeared on our sister publication PC-WELT and was translated and localized from German.




