Accidentally downloading malware can be a frightening experience, but what’s even more alarming is allowing it to remain on your computer, causing damage over time. That’s why, as soon as you suspect or discover your system may be infected, immediately follow these steps to secure your data.
The first and most crucial step you should take when you suspect malware has infiltrated your system is disconnecting your device from the internet. This prevents malware from spreading further, communicating with remote servers, stealing personal data, or allowing threat actors to spy on you.
So, if your computer warns you of a potential infection, immediately cut off the internet connection. If you’re using Ethernet, unplug the cable, or if connected via Wi-Fi, click the Wi-Fi icon in the bottom-right corner to disconnect. Stay offline until you’ve properly assessed and removed the malware.
2 Boot Into Safe Mode
After disconnecting your device from the internet, the next step is to boot your Windows PC into Safe Mode. Safe Mode runs your system with minimal resources and only the necessary drivers. This prevents the malware from spreading and reduces the chance the infection will interfere with antivirus scans or any corrective actions, making it easier to remove the malware.
To boot into Safe Mode, go to Settings > System > Recovery, and click “Restart Now” under Advanced Startup. After your system restarts, navigate to Troubleshoot > Advanced Options > Startup Settings > Restart. Once your PC restarts, press “4” or “5” to select Safe Mode with Networking or Safe Mode.
3 Run a Malware Scan and Remove Infections
Once you’ve booted your system into Safe Mode, it’s time to remove the malware. First, run a full system scan with Windows Defender to see if any threats are quarantined or deleted. Then, perform a second scan with a third-party antivirus like Malwarebytes to check all files, programs, and processes for signs of malware.
Together, these scans will detect and remove any malicious files or software. Ensure your antivirus tool is up-to-date, as outdated versions might not catch newer threats.
4 Check for Unusual Installed Programs
While malware scans can remove infections, some advanced malware may disguise itself as legitimate software running in the background. To ensure nothing harmful is left behind, you should manually check your system for suspicious or unauthorized programs that may have been installed without your knowledge.
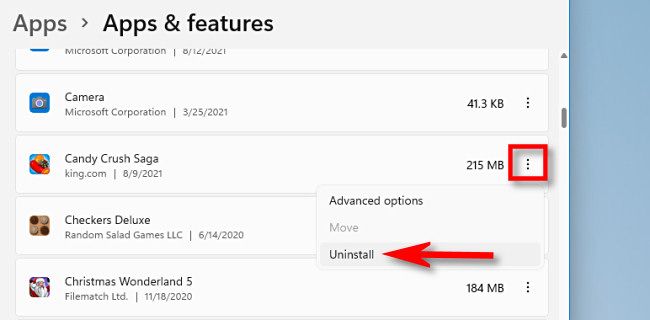
This step will help prevent any hidden malware from relaunching. To do this, open the Settings app and go to Apps > Installed Apps. Carefully review the list for any unfamiliar programs. If you spot anything suspicious that appeared after your PC was infected, click on three vertical dots and click “Uninstall” to remove the app immediately.
5 Keep an Eye on Task Manager for Unusual Resource Usage
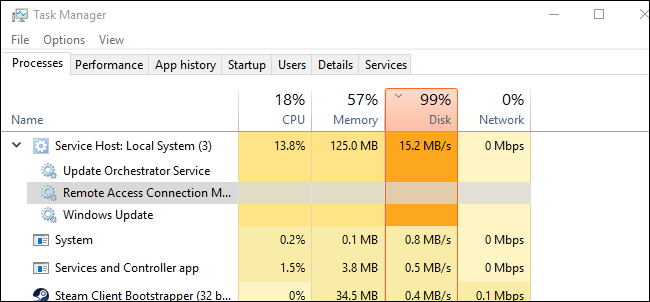
Some malware, like cryptojackers, is designed to hijack your computer’s processing power to mine cryptocurrency or run other resource-intensive operations. These programs run quietly in the background, consuming CPU, memory, or disk resources, which can slow down your system. You can use the Task Manager to identify any suspicious activity.
To do this, right-click the taskbar and select “Task Manager.” Navigate to the “Processes” tab and sort processes by CPU, RAM, or Disk usage. If you notice any processes using unusually high resources, right-click on them and choose “Open File Location.” You can delete the source file from there to stop the resource drain.
Some Windows processes have unusual names and use high resources. Before deleting files, research the process online to ensure you aren’t removing a critical system file.
6 Inspect Startup Apps
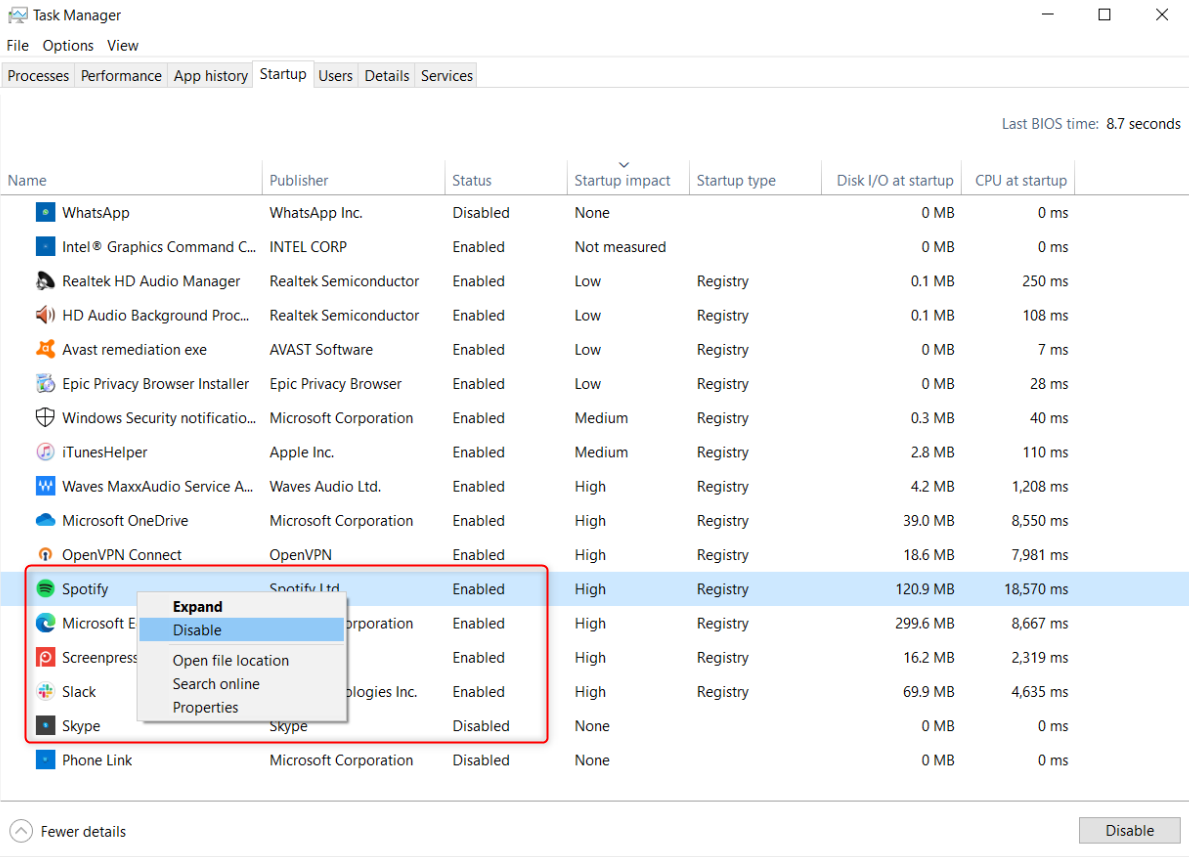
Malware can hide in startup programs, launching automatically whenever you boot your computer. Reviewing these startup apps helps identify any malicious software running without your knowledge. Once you’ve verified a process is malicious—by researching it online—you can confidently disable it.
To do this, right-click the Start button and select “Task Manager.” In the Startup tab, find any unfamiliar or suspicious apps, right-click on them, and select “Disable” to prevent them from starting up. You can also right-click and select “Open File Location” to check the source file of the process.
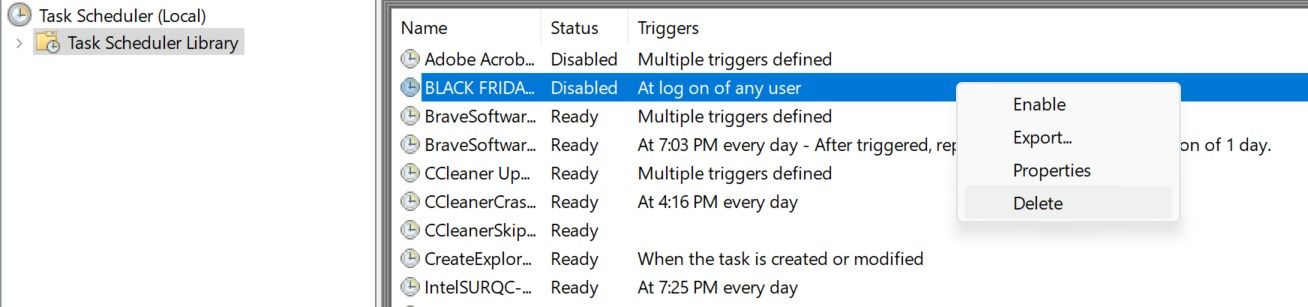
7 Check Task Scheduler
Malware can be programmed to schedule tasks that run automatically. These tasks continue working even after the original infection has been removed from your device. That’s why you must review the Task Scheduler to identify any malicious tasks that may still be being executed in the background.
To do this, press Windows+R, type taskschd.msc, and hit Enter. Examine the Active Tasks list in the Task Scheduler Library and explore individual folders to find tasks set to initiate suspicious actions. Delete those you don’t recognize. Right-click on the task and select “Delete.” You can check which scripts are associated with each task in the Actions tab.
8 Ensure You’re Not Being Monitored
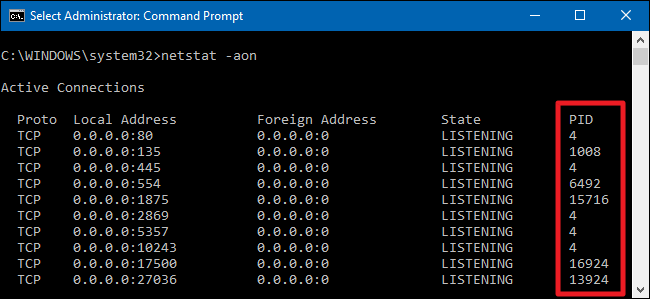
Cybercriminals can also use malware to spy on victims. This type of malware can track your keystrokes, steal personal information, monitor your activities, or even record you through your webcam, potentially leading to blackmail. Therefore, you must verify that no threat actor has established a remote connection to your computer and is monitoring you.
To check for this, obtain a list of active connections: open Command Prompt as an administrator and enter netstat -an. Then, review all current network connections and look for any suspicious IP addresses. You can then verify if those connections belong to legitimate companies whose services you use and disconnect any that seem suspicious.
9 Check Your Browser for Signs of Infection
The Internet is the primary source of malware infections, and we primarily access it through a web browser. So, you must ensure that malware hasn’t hijacked your browser to monitor your online activity, inject ads, or redirect your searches. To verify this, look for signs indicating your browser has been compromised.
Check for any unfamiliar or suspicious extensions and remove them right away. Change your default search engine to prevent redirection to malicious sites. Malware can store harmful cookies or cache data to track your activity, so clear your cookies and cache. If you encounter unusual pop-up ads while browsing, delete the browser app and reinstall it.
Here’s what I do whenever I suspect I’ve been tricked into downloading an email attachment, a deceptive file, or clicking on a malicious link on an infected website. While these steps stop the spread of infection, continue monitoring your computer for a few days. If you notice anything unusual, run additional scans, perform a System Restore, or factory reset your OS.