Security researchers have discovered 75 applications on Google Play and another ten on Apple’s App Store engaged in ad fraud. Collectively, they add to 13 million installations.
Apart from flooding mobile users with advertisements, both visible and hidden, the fraudulent apps also generated revenue by impersonating legitimate apps and impressions.
Although these types of apps are not seen as a severe threat, their operators can use them for more dangerous activity.
Researchers from HUMAN’s Satori Threat Intelligence team identified a collection of mobile apps that are part of a new ad fraud campaign that they named ‘Scylla’.
The analysts believe Scylla is the third wave of an operation they found in August 2019 and dubbed ‘Poseidon’. The second wave, apparently from the same threat actor, was called ‘Charybdis’ and culminated towards the end of 2020.
Ad-fraud apps
The Satori team have informed Google and Apple about their findings and the apps have been removed from the official Android and iOS stores.
On Android devices, unless you have the Play Protect security option disabled, the apps should be detected automatically.
For iOS, Apple is not clear on how to remove adware apps already installed on the device. Human is recommending users remove the fraudulent apps if present on their devices. A short list with the most downloaded of them is present below:
iOS app list:
- Loot the Castle – com.loot.rcastle.fight.battle (id1602634568)
- Run Bridge – com.run.bridge.race (id1584737005)
- Shinning Gun – com.shinning.gun.ios (id1588037078)
- Racing Legend 3D – com.racing.legend.like (id1589579456)
- Rope Runner – com.rope.runner.family (id1614987707)
- Wood Sculptor – com.wood.sculptor.cutter (id1603211466)
- Fire-Wall – com.fire.wall.poptit (id1540542924)
- Ninja Critical Hit – wger.ninjacriticalhit.ios (id1514055403)
- Tony Runs – com.TonyRuns.game
Android app list (1+ million downloads)
- Super Hero-Save the world! – com.asuper.man.playmilk
- Spot 10 Differences – com.different.ten.spotgames
- Find 5 Differences – com.find.five.subtle.differences.spot.new
- Dinosaur Legend – com.huluwagames.dinosaur.legend.play
- One Line Drawing – com.one.line.drawing.stroke.yuxi
- Shoot Master – com.shooter.master.bullet.puzzle.huahong
- Talent Trap – NEW – com.talent.trap.stop.all
The full list of applications part of the Scylla ad-fraud wave is available in HUMAN’s report.
Malware details
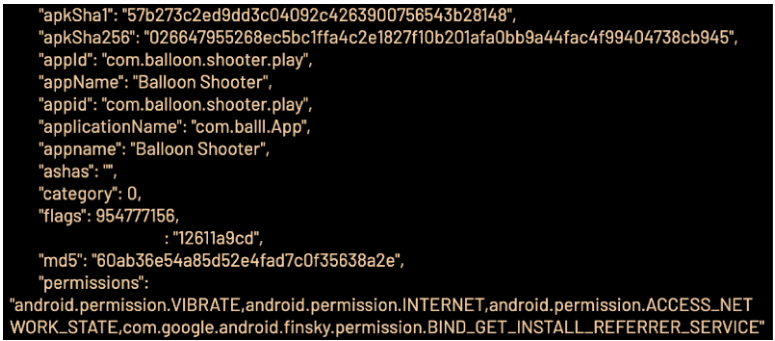
The Scylla apps typically used a bundle ID that doesn’t match their publication name, to make it appear to the advertisers as if the ad clicks/impressions come from a more profitable software category.
HUMAN’s researchers found that 29 Scylla apps imitated up to 6,000 CTV-based apps and regularly cycled through the IDs to evade fraud detection.
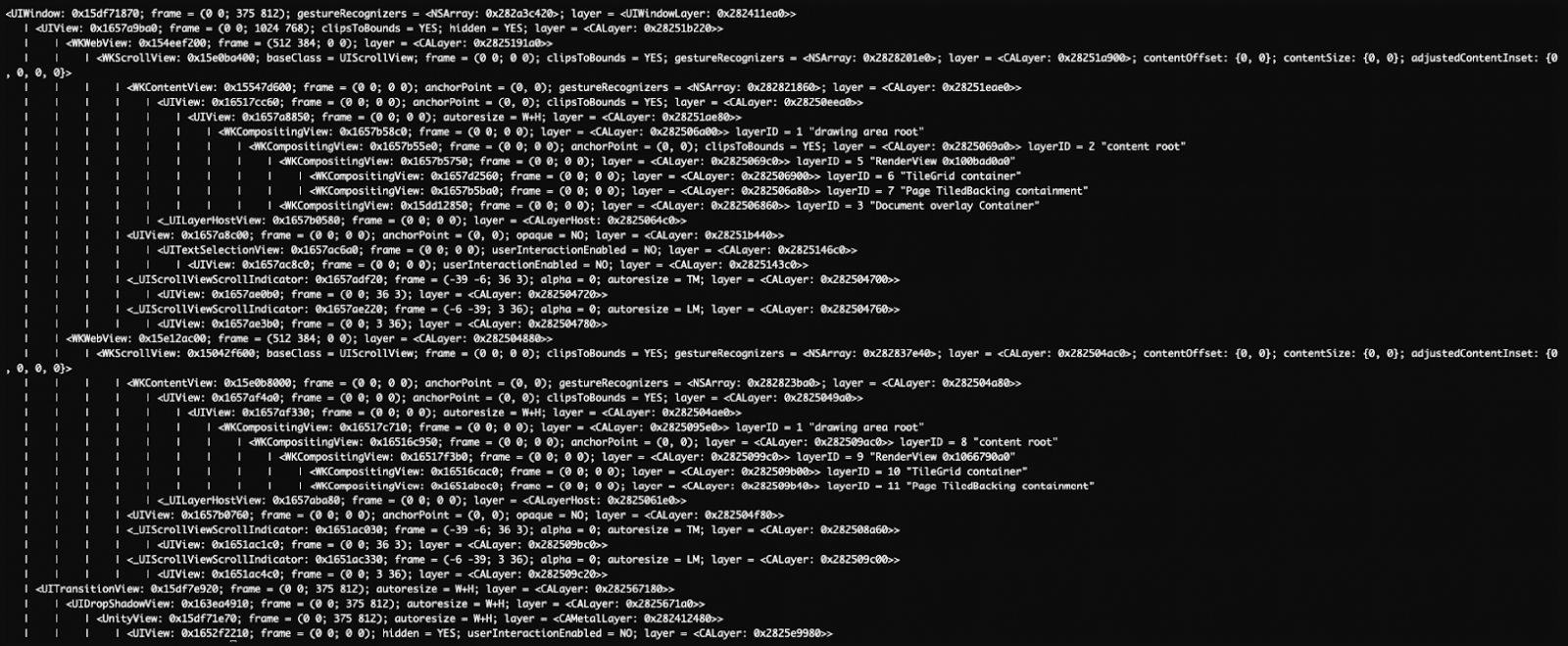
On Android, the ads are loaded in hidden WebView windows, so the victim never gets to notice anything suspicious, as it all happens in the background.
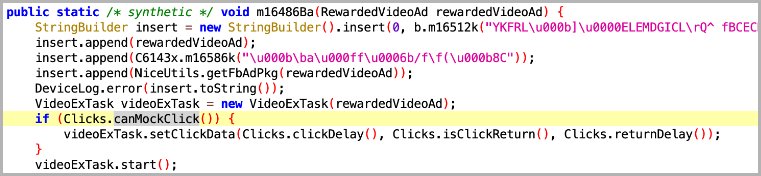
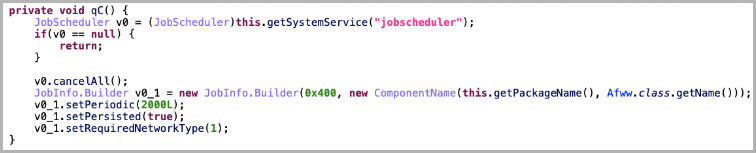
Additionally, the adware uses a “JobScheduler” system to trigger ad impression events when the victims aren’t actively using their devices, for example, when the screen is off.
The signs of fraud are registered in logs and can be seen in network packet captures, but regular users do not typically scrutinize these.
Compared to ‘Poseidon’, the first campaign for this operation, Scylla apps rely on additional layers of code obfuscation using the Allatori Java obfuscator. This makes detection and reverse engineering more difficult for researchers.
Users should monitor their apps for malicious or unwanted apps by looking for some signs that typically indicate an issue such as rapid battery drainage and increased internet data usage, or apps you don’t remember installing.
It is also recommended to check the list of installed apps and remove those you don’t remember installing or come from an unfamiliar vendor.





