Key Takeaways
- Encrypting your drive secures your files from unauthorized access with a password, even if the drive is physically removed.
- VeraCrypt is an easy-to-use, open-source encryption software suitable for beginners.
- Encrypting a drive on Linux is as simple as downloading VeraCrypt and running through the steps of its encryption wizard.
One of the best ways to secure a laptop or desktop computer is to encrypt your hard drive or, failing that, a partition. We go over how you can encrypt a Drive on Linux using VeraCrypt, a free program.
Why Encrypt a Drive?
Encrypting your drive or drives is a foundational part of computer security. It makes it so nobody except you or whomever you share the password with can get access to your files. Even if the drive in question is removed from the device, it still can’t be accessed.
In my article on how to make your laptop more secure, I recommend that you always encrypt your drive using Linux’s built-in tool which prompts you during the installation process. However, if you decided to skip this step and changed your mind, or just want to encrypt a section of your hard drive, you’ll have to use third-party software. This is where VeraCrypt comes in.
What Is VeraCrypt?
VeraCrypt is a popular open-source encryption tool that’s used by security professionals as well as everyday people. It’s a fork (a program that runs on the same source code) of the once-popular TrueCrypt, which was discontinued by its developer. It’s fast, secure, very easy to use, and will run on just about any system: we also used it for our article on encrypting your Windows system drive.
That said, VeraCrypt is far from the only TrueCrypt alternative out there. There are plenty of other options you can pick from, but for people new to this type of software VeraCrypt is an easy way to get started.
How to Encrypt a Linux Drive with VeraCrypt
Note that encrypting an entire drive can have serious repercussions on your system. If you just need to encrypt a few files, I recommend you just encrypt a folder, instead.
To start, you first need to install the program. Go to the VeraCrypt download page and select your distro of choice. For the purposes of this guide we’re using the GUI version, but you can download the console version if you prefer.
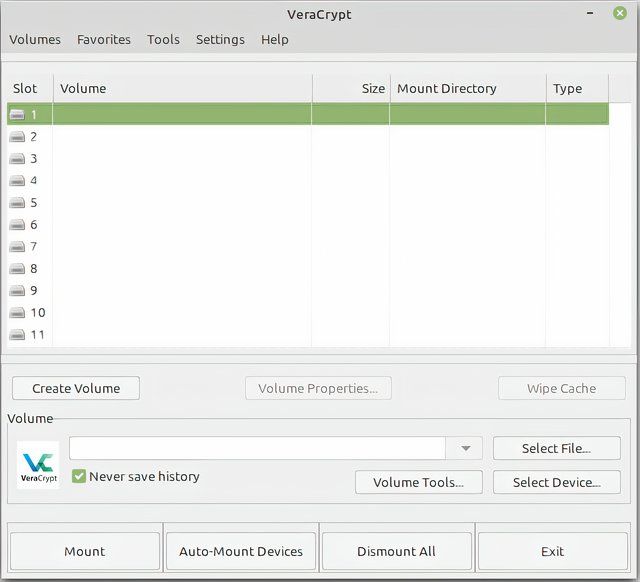
Once the package is downloaded and installed, start the program. You’ll see the below screen, which isn’t very clear at first glance.
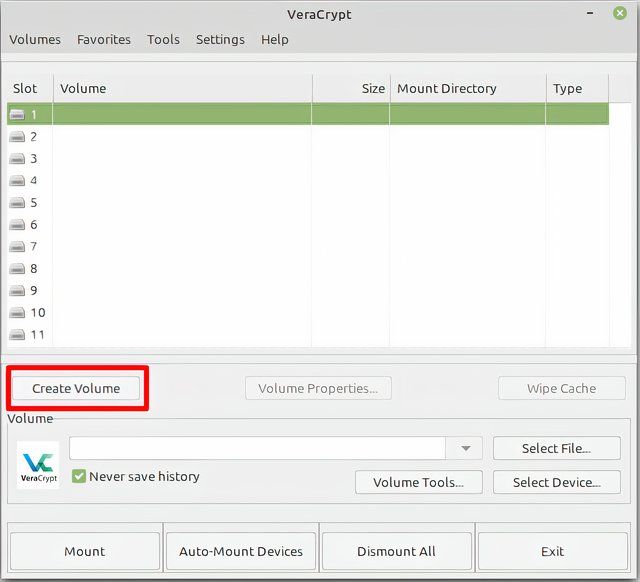
Anything VeraCrypt encrypts—be it a folder, partition, or entire drive—it refers to as a volume or a container (because you put things into it). To get started, we first need to click on “Create volume” on the lower left.
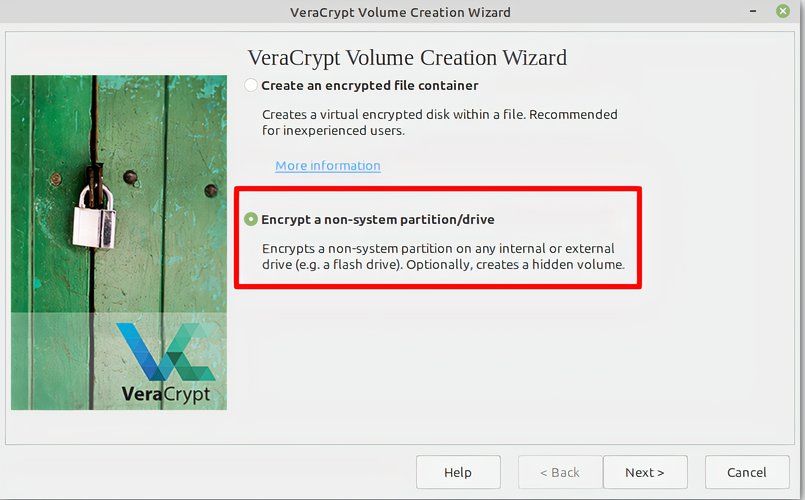
This starts the VeraCrypt wizard which will guide us through the rest of the process step by step. You just enter your choice and confirm by clicking on “Next.” Since we’re creating a partition, we need to select the second option, “Encrypt a non-system partition or drive.”
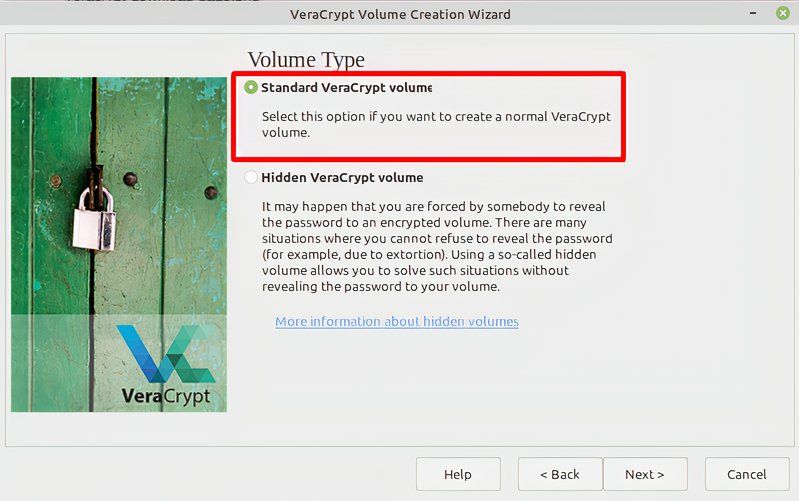
You now get the choice to create a standard or hidden volume. Unless you’re very worried about physical security, I would keep it to the default (standard). If you’re not sure, you can read VeraCrypt’s explanation of how hidden volumes work, linked in the wizard.
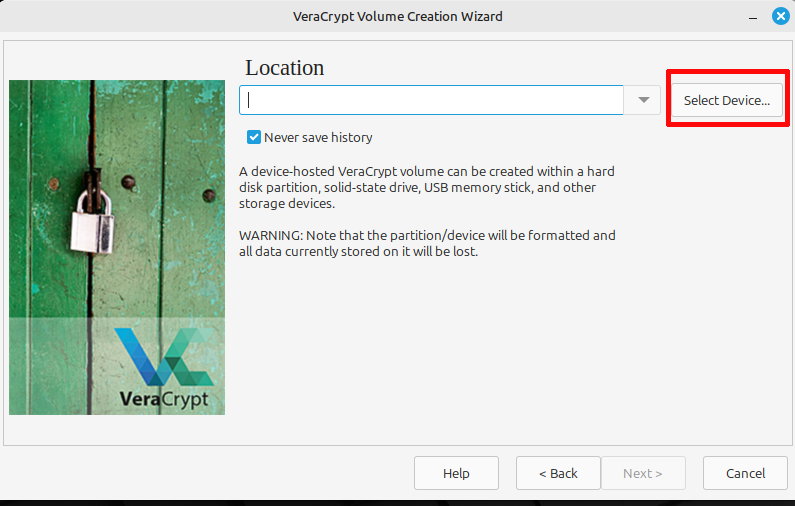
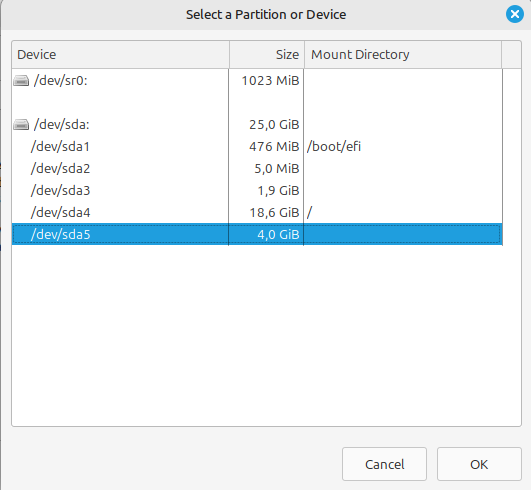
On the next screen, click on “Select device” in the top right to pick the drive you want to encrypt. You’ll get a list of all the partitions on your device.
For the purposes of this article I set up a virtual machine with custom partitions. However, it’s likely you’ll need to set some up for yourself, check out our guide on how to manage partitions in Linux if you need help. Whatever you do, do not encrypt your file or boot drives! It will make your system unusable.
Also note that the drive needs to be unmounted. I used the “lazy option” from our Linux mounting guide.
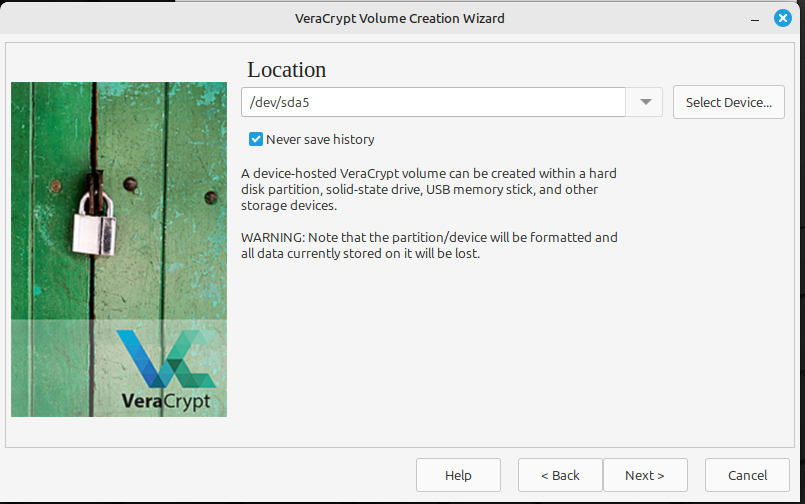
Once you’ve selected the drive you want to encrypt, check you entered it correctly and hit “Next.”
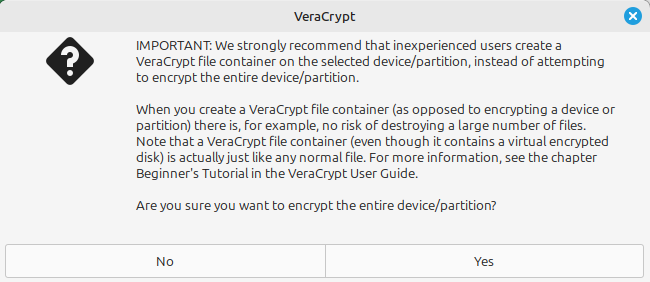
You’ll be warned that encrypting an entire drive is pretty drastic and that you can choose to just create an encrypted folder instead. Choose “Yes” to throw caution to the wind and enter your Linux admin password.
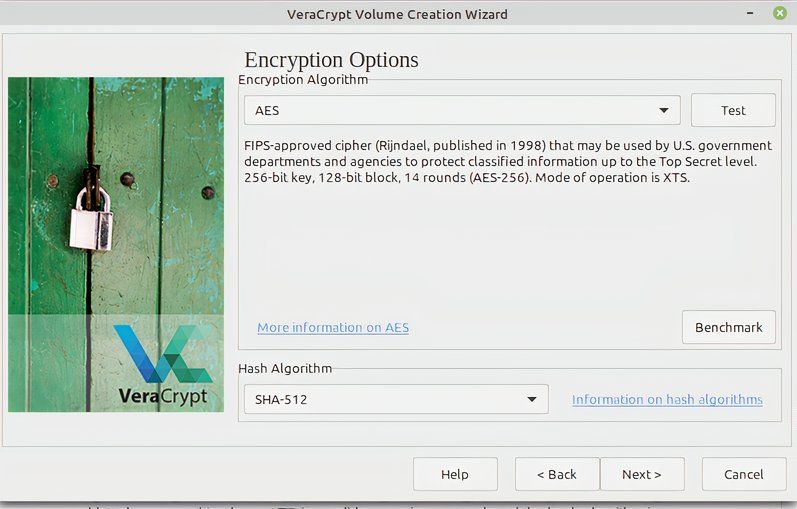
With all that done, you need to pick the level of encryption. Unless you have specific requirements, I advise you to stick with the defaults here. AES is a reliable protocol and much the same goes for the hash.
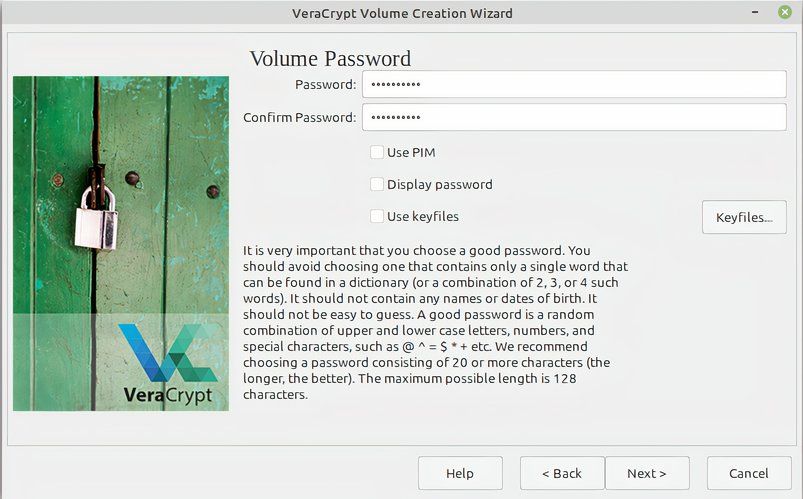
Now you set the password. Make sure it’s both memorable and strong, and store it somewhere safe. We recommend some great password managers you can use. Ignore all the other options here.
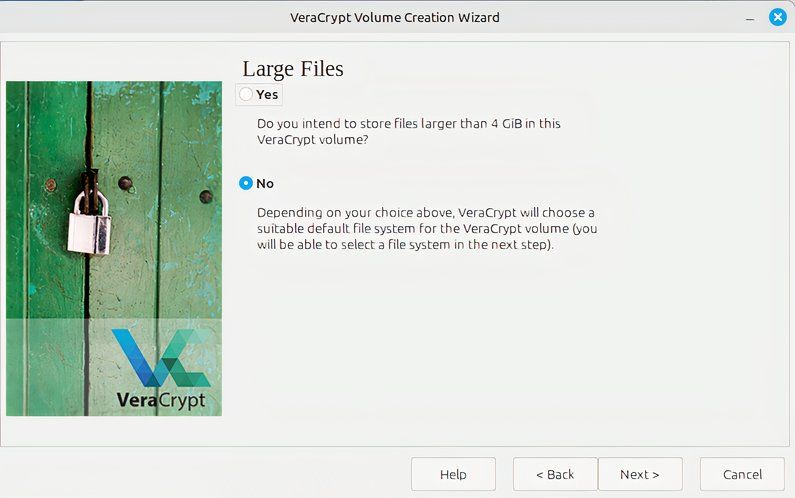
In the next screen you’ll be asked the size of the files you’ll be using as this affects the file system VeraCrypt is using. Choose the option that’s best for you; I went with “No.”
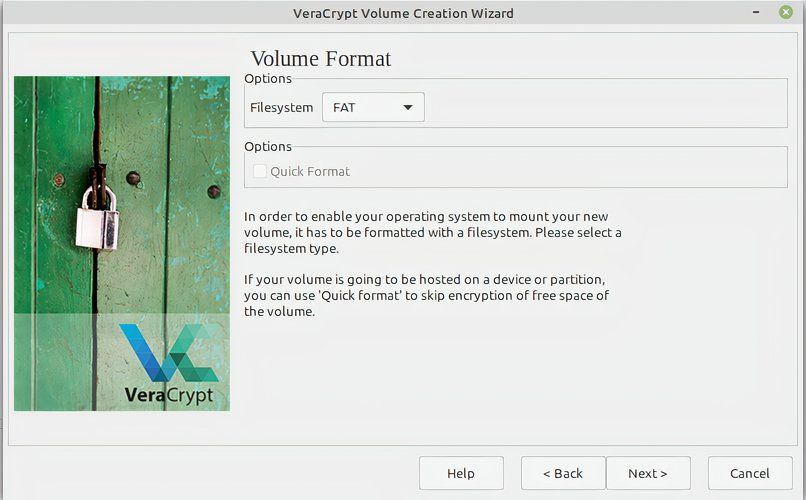
The penultimate step is choosing the file system. Your previous choice influences the default here, so I would just stick with what VeraCrypt recommends—FAT in my case.
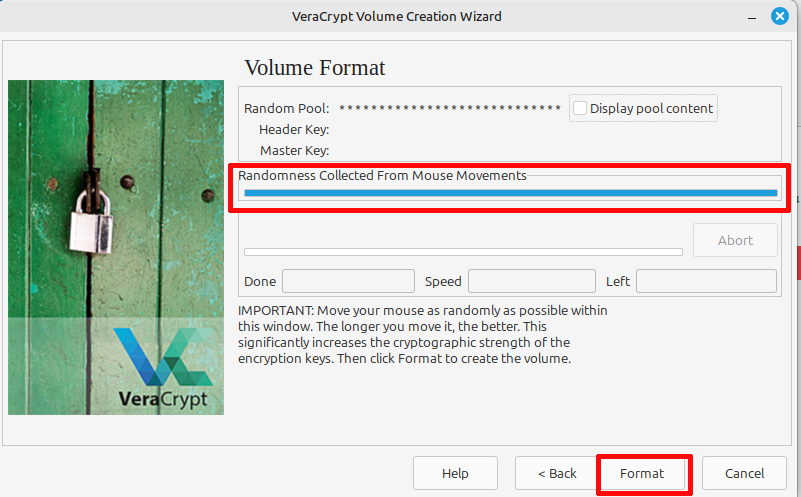
Now comes a fun little quirk of VeraCrypt’s: to make the encryption key more random—and thus stronger—you need to shake your mouse pointer around for a while, up to a minute. Once the bar in the center of the screen fills up, hit “Format” at the bottom of the window. You’ll get another warning, hit “Yes.”
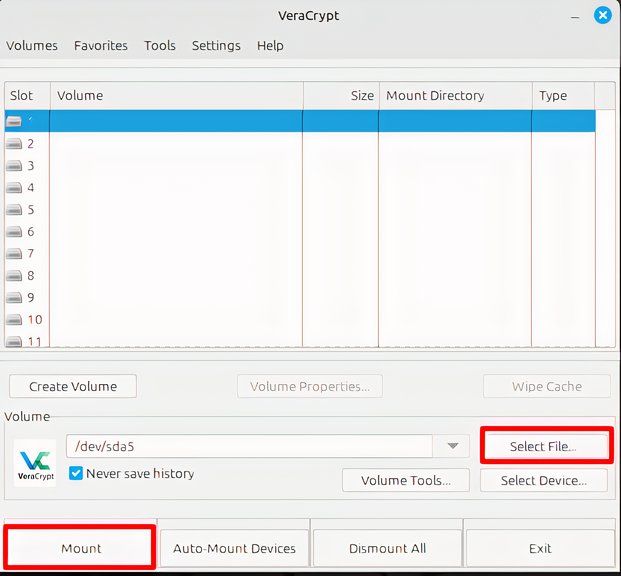
Once that’s done, that’s it for volume creation. Exit the wizard and go to the main screen of VeraCrypt again. There, click “Select device,” find the drive you encrypted, and then click on “Mount” in the bottom left of the screen.
You’ll need to enter the password you created earlier for the volume. VeraCrypt will do some work and your drive is ready for use. You can move files to and from it, though you will have to open it from VeraCrypt’s interface every time.
Creating an encrypted drive in Linux is made fairly easy thanks to VeraCrypt. I realize it looks like a lot to keep in mind, but once you have a drive partitioned it becomes pretty easy and you should be able to get it done in under 15 minutes or so. The reward is a lot of secure storage space.