Key Takeaways
- Kali Linux is a Debian-based distribution packed with hundreds of tools for penetration testing and computer forensics.
- Kali Linux is not for casual users; it requires knowledge and experience to use its powerful tools effectively.
- If you’re new to Linux, consider Ubuntu or Linux Mint for everyday use before exploring Kali Linux.
Kali Linux is a name that often surfaces in conversations about ethical hacking and penetration testing. But what exactly is it, and is it the right for you? Let’s explore what makes Kali Linux stand out and whether it fits your needs.
My Intro to Kali Linux
Let me take you back to when I first discovered Kali Linux. I was beginning to learn cyber security, trying to figure out which direction I wanted to take, and everywhere I turned, people were talking about Kali.
So, I did what any curious tech enthusiast would do—I installed it, fired it up, and was immediately hit with a barrage of tools with names like “BeEF,“ “Bettercap,” “Hashcat,” “Metasploit,” and “Nmap,” It felt like I’d just opened Pandora’s box.
Kali is a powerful tool that requires a solid understanding of what you’re doing. But what exactly is Kali Linux, and why does it have such a reputation as a top choice for ethical hackers and penetration testers?
What Is Kali Linux?
Kali Linux, previously known as BackTrack Linux, is an open-source, Debian-based Linux distribution developed by Offsec. It is designed specifically for penetration testing and is packed with hundreds of tools for computer forensics, reverse engineering, and vulnerability detection.
Because Kali is built on Debian, it’s incredibly stable and secure. This Debian base means that Kali benefits from a vast repository of software and a familiar package management system. If you’ve used other Debian-based distributions like Ubuntu, you’ll find that Kali isn’t too tough to navigate. It’s definitely not designed for Linux beginners, but if you’re up for the challenge, there’s a lot you can learn.
Offsec has ensured that Kali isn’t just about the tools; it’s about giving you a free, open-source, and always-evolving platform. Every piece of software is available for tweaking, and Kali’s commitment to open-source development means the entire Git tree is accessible to anyone interested.
Who Typically Uses Kali Linux?
Now, if you’re imagining a scene from Mr. Robot or thinking of a room full of hackers in hoodies, you’re not entirely wrong. But the truth is, Kali Linux isn’t just for Hollywood hackers. It’s for professionals who need to simulate network attacks to find and fix vulnerabilities before the bad guys do.
When I first started learning penetration testing, I quickly realized that Kali was the go-to operating system for ethical hackers. Whether they’re working in a corporate environment, testing the security of a company’s network, or teaching the next generation of pentesters, Kali is their Swiss—well, it’s their toolkit of choice.
Key Features of Kali Linux
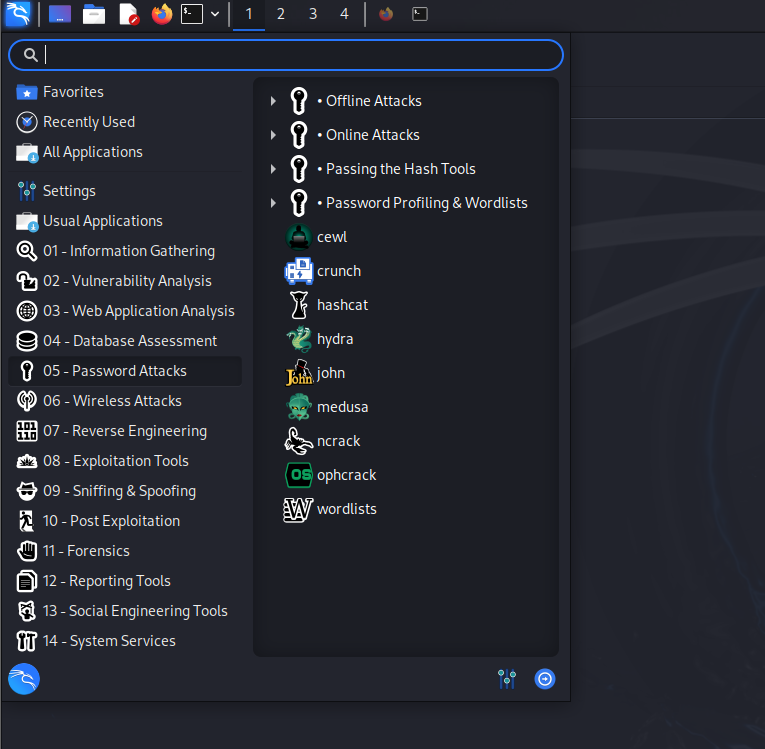
Kali Linux comes equipped with a wide range of tools organized into categories like information gathering, vulnerability analysis, wireless attacks, password cracking, and social engineering, making it suitable for all aspects of penetration testing.
One of the moments that made me appreciate Kali was when I started exploring its pre-installed tools. It’s like opening a toolbox and finding every tool you could possibly need for the job.
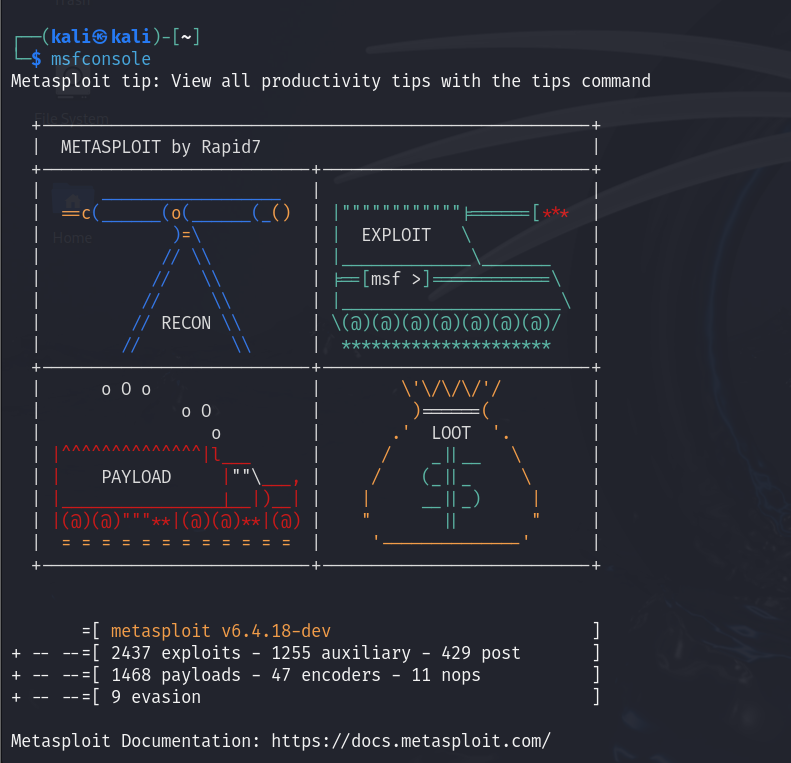
Need to scan a network for open ports? Nmap’s got you covered. Looking to exploit a vulnerability? Metasploit is right there. Want to dive deep into network traffic? Fire up Wireshark. Tools like Wifite and Airgeddon are also pre-installed if you’re interested in Wi-Fi security. Wifite automates the process of cracking Wi-Fi passwords, while Airgeddon provides a versatile environment for assessing wireless security.
The development team didn’t forget about the nitty-gritty details. For example, they’ve included a custom kernel customized for packet injection, which is key when working with Wi-Fi. Plus, every package is signed by GNU Privacy Guard (GPG), ensuring you’re working with secure software.
Why Kali Linux Is Not for Everyone
But here’s the thing: Kali Linux isn’t for everyone. When I started using it, it was challenging. The tools in Kali are powerful, but they require knowledge and experience to be used effectively. You could easily get in over your head if you’re not careful.
For example, I remember running a network scan on my home network to see what I’d find. It was a fascinating experience, but I quickly realized how easy it would be to cause problems if I didn’t know exactly what I was doing. The tools in Kali are not toys; they’re powerful and can have serious consequences if misused.
Imagine that you execute a script without understanding what it does—a classic move by so-called “script kiddies” in cyber security. Your actions could lead to serious consequences, potentially even legal trouble. And trying to explain it away with an excuse like “I’m sorry, I didn’t know what I was doing” won’t get you off the hook.
And honestly, Kali isn’t designed for everyday tasks. You could use it as your main operating system, but why would you? It’s not optimized for web browsing, document editing, or watching movies.
Alternatives for Casual Users
If you’re just curious about Linux or want to explore it for everyday use, there are way better options out there. When I first got into Linux, I started with Ubuntu, and it was a great introduction. It’s user-friendly, has a massive community for support, and can handle all the regular tasks you’d expect from an operating system.
Linux Mint is another solid choice, especially if you’re used to a more traditional desktop layout. And if you’re coming from Windows, Zorin OS might feel like a comfortable middle ground. These distributions are designed for everyday use, so you can browse the web, work on documents, and even play games without worrying about accidentally launching a network attack.
Geting Started with Kali
So, if you’ve decided that Kali Linux is the right tool for you, the next step is to get hands-on. You can download Kali Linux directly from the official website, where you’ll find options for different installation methods, whether you want to run it on your main machine, as a virtual machine, or even from a USB stick.
If you’re new to Linux, consider trying Kali on a virtual machine first. Solutions like VirtualBox or VMware allow you to install Kali in a controlled environment where you can experiment without affecting your main operating system. Check out How to Install Linux in VirtualBox for a step-by-step guide.
If you’re ready to explore Kali further, I recommend checking out this Kali Linux Tutorial. It provides a comprehensive guide on installing, configuring, and using Kali effectively.