Key Takeaways
- Linux Unified Key Setup (LUKS) is a disk encryption specification for Linux.
- LUKS uses a master key to encrypt data, with passphrases unlocking the key.
- LUKS protects user data on block devices, including laptops and external drives, from theft.
Came across the term “LUKS” but don’t know what it does or how it relates to Linux? If you’re someone concerned about safeguarding your data, then having LUKS set up is essential for you. In this guide, I’ll explain how LUKS works and how it helps you secure your important data.
What Is LUKS on Linux?
Linux Unified Key Setup (or LUKS for short), is a disk encryption specification widely used in Linux systems. Created by Clemens Fruhwirth in 2004, it’s designed to provide a standardized encryption mechanism that’s both secure and user-friendly. It protects data by encrypting it inside physical and logical disk partitions so that only authorized users can access the content of that encrypted partition. You can think of it as similar to Windows BitLocker.
LUKS operates on a block level. It encrypts whole partitions or disks rather than individual files. It uses strong encryption algorithms like AES (Advanced Encryption Standard). It uses the partition header to store the necessary setup information such as the encryption algorithm and key size. This header is what sets LUKS apart from dm-crypt. If the header becomes corrupted, you won’t be able to decrypt the device.
How LUKS Works
LUKS encryption creates an encrypted container called LUKS volume on a disk partition. It uses symmetric algorithms such as AES to encrypt the volume which can only be accessed using a passphrase. When you unlock the LUKS volume, it becomes accessible like a regular block device. So you can read from it and write to it.
LUKS stores its encryption metadata in a special section at the beginning of the encrypted partition called the LUKS header. This header contains some critical information such as the cipher and mode, hash function, and key slots. The actual encrypting of the partition is done using a master key. This master key is randomly generated when the LUKS setup is initialized. This master key is what directly encrypts and decrypts the data on the partition. The passphrase doesn’t encrypt the data. Instead, it encrypts the master key stored in the key slots.
If you want to access the encrypted data, LUKS requires you to enter a passphrase. This passphrase is then used for decrypting the master key stored in one of the key slots. After the master key is decrypted, that key in turn is used to decrypt the data on the partition.
Why You Should Use LUKS
The primary reason for using LUKS is to protect user data. LUKS can encrypt whole block devices, making it suitable for protecting the data in mobile devices like laptop disk drives and removable media. Since the content of the encrypted block devices is arbitrary, it’s also good for encrypting swap devices.
LUKS is commonly used for full disk encryption. You can encrypt the root partition of your Linux system during installation so that no one without authorization can access the system files. You may also encrypt the boot partition in the Linux system to protect against tampering with the Linux kernel. If you’re using systemd, then you can also encrypt individual home directories.
LUKS supports multiple key slots, giving you the opportunity to assign different passphrases for the same encrypted partition. So, if you have a multi-user setup, each user can have an individual decryption key without needing to share a common passphrase. Moreover, if one passphrase is forgotten, other ones can be used to access the data.
It protects your device from physical theft. Even if your laptop, external hard drive, or other storage devices are stolen, the data inside remains inaccessible without the correct decryption key.
It Has Some Catches
One of the biggest drawbacks of using full disk encryption lies in performance issues. Decrypting data on the fly requires processing power, resulting in slower read-write speeds. If you have modern hardware, the difference might be negligible sometimes, but it’s not totally out of the question. You’ll also experience increased boot time because the system needs to decrypt the entire drive before fully loading the operating system. You can read more about this in this Reddit thread and this benchmark test.
Another important note is that LUKS disk encryption will only protect your data when your system is turned off. If your laptop is stolen while it’s powered on and the drive is already decrypted, the thief could potentially access your data without needing to bypass the encryption. Once decrypted, anyone has access to the files on that drive.
Setting up LUKS encryption is not an easy process on pre-installed Linux systems. It requires a full backup so that you can restore important data in case you lose it. Speaking of backups, encrypted backups need careful handling. If you lose your decryption key, you may never recover your data.
How to Set Up LUKS Encryption
The easiest way to set up LUKS full disk encryption is when you first install Linux. Let me show you how on Ubuntu 24.04.
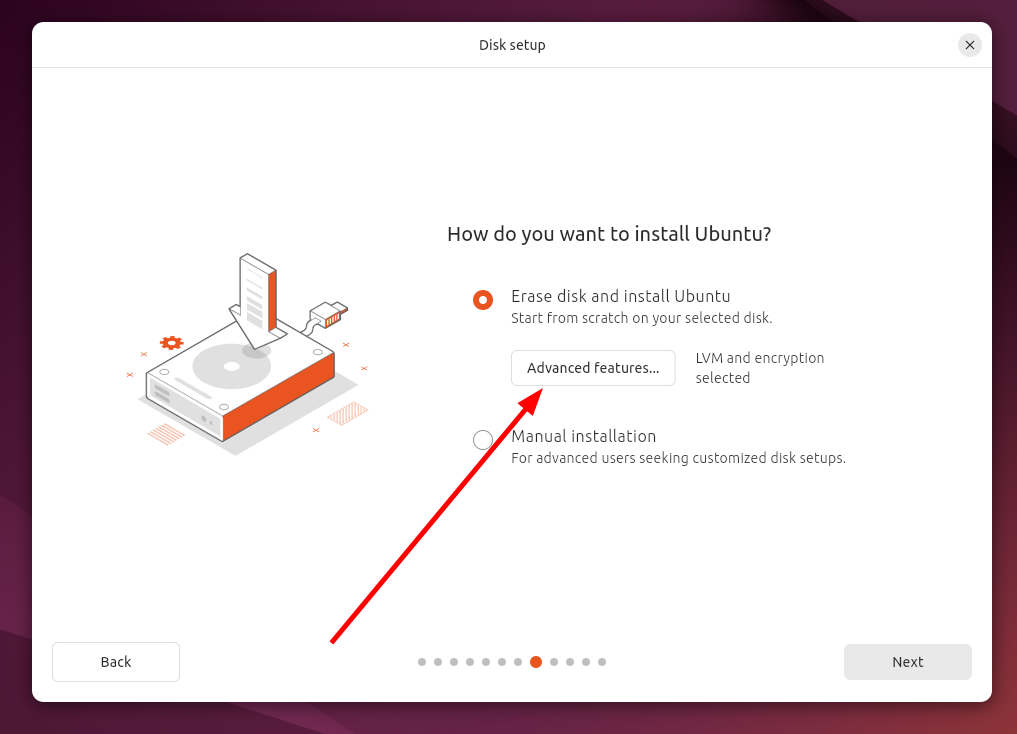
During the installation, you should see a disk setup prompt. Press “Advanced Features.”
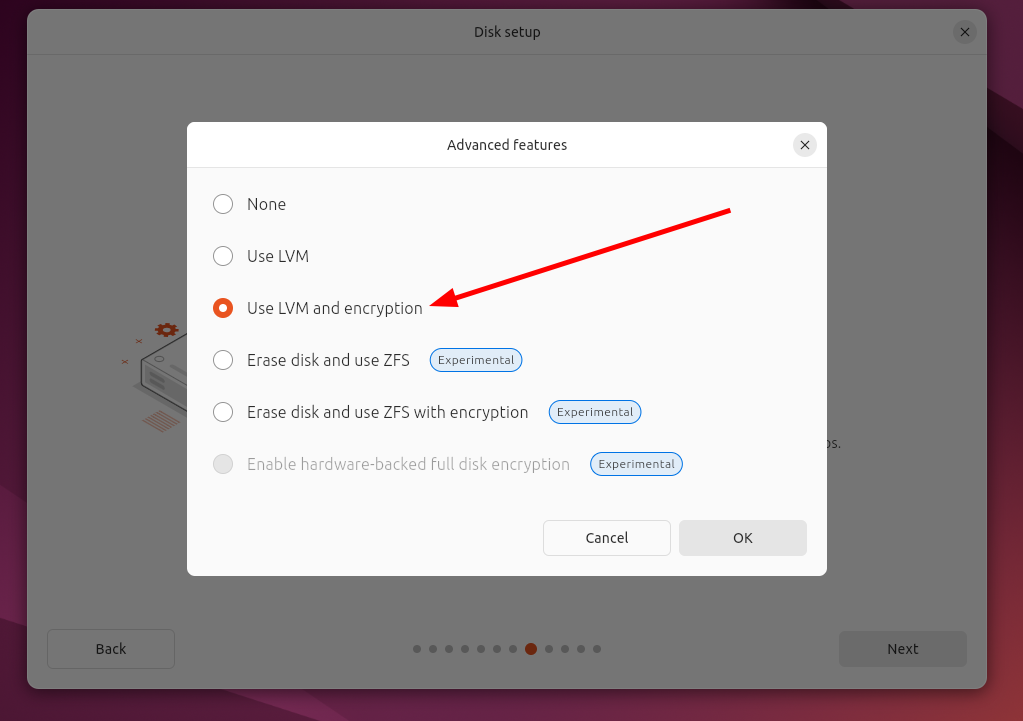
From the list, select “Use LVM and Encryption.” Press “OK.”
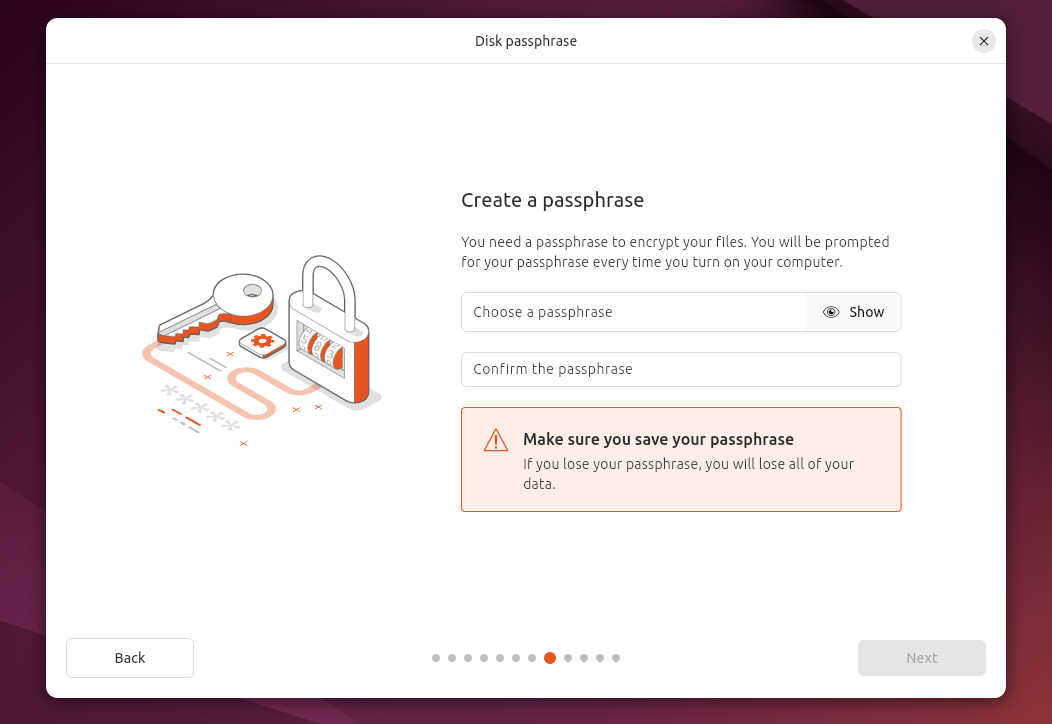
Press the “Next” button to proceed. On the next screen, you’re asked to create a passphrase. Enter a secure passphrase on both fields and press “Next.”
Then continue with the rest of the installation.
If you don’t want to re-install Linux, there’s a utility called cryptsetup to set up encrypted file systems. You may need root privileges to run some of the commands. First, you’ll need to install it. On Debian/Ubuntu, run:
sudo apt install cryptsetup
List your available partitions using the following commands:
sudo fdisk -lblkid
Find out the partition you want to encrypt from the list.
Next, use the cryptsetup utility to encrypt your chosen partition in the following way:
cryptsetup -y -v luksFormat /path/to/partitioncryptsetup -y -v luksFormat /dev/xvdc # For example
You’ll be asked to confirm that you want to overwrite the partition and then enter a passphrase. You must save and remember the passphrase because it’s not recoverable.
The above command will wipe all data on the partition. Make sure to back up any important data.
After that, create a logical mapping by running:
cryptsetup luksOpen /path/to/partition partition_namecryptsetup luksOpen /dev/xvdc backup_partition # For example
Enter the passphrase when prompted. This will initialize the volume. To see the mapping details, run:
ls -l /dev/mapper/backup_partition
To see the mapping status, use:
cryptsetup -v status backup_partition
Then, use cryptsetup to see whether the device has been formatted correctly for encryption.
cryptsetup luksDump /path/to/partitioncryptsetup luksDump /dev/xvdc # For example
Use the dd command to allocate block data with zeros to the LUKS-encrypted partition:
dd if=/dev/zero of=/dev/mapper/backup_partition
Once done, format the new partition with this command:
mkfs.ext4 /dev/mapper/backup_partition
I’ve used the ext4 file system here. You can use your preferred one. Lastly, mount the new file system.
mkdir /backup2
mount /dev/mapper/backup_partition /backup_partition
df -H
cd /backup_partition
ls -l If you want to change the passphrase for the encrypted partition, then run the below commands:
cryptsetup luksDump /dev/xvdc # Using /dev/xvdc as an examplecryptsetup luksAddKey /dev/xvdc # Using /dev/xvdc as an example
You’ll be prompted to enter a new passphrase and then confirm it.
By implementing LUKS, you can ensure better security for your confidential data. It’s also suitable for devices used by multiple users. You can take many other measures to make your Linux device more secure.