A macOS vulnerability exposed Apple devices to severe security risks by bypassing System Integrity Protection, but a security patch has killed the exploit.
On January 13, 2025, Microsoft Threat Intelligence revealed a critical vulnerability in macOS — CVE-2024-44243 — that bypasses Apple’s System Integrity Protection (SIP) by exploiting third-party kernel extensions. This issue, now patched, could have allowed attackers to compromise macOS security at its core.
System Integrity Protection (SIP) is a macOS security feature designed to safeguard critical system files and processes. It restricts even users with administrative privileges from making changes that could compromise the operating system’s stability and security.
SIP protects sensitive system files, prevents arbitrary kernel code execution, and ensures apps can’t load unauthorized kernel drivers.
CVE-2024-44243 showed how attackers could bypass SIP protections by loading malicious third-party kernel extensions called rootkits. Rootkits grant unauthorized access, install persistent malware, bypass user permissions, and tamper with security mechanisms.
How CVE-2024-44243 works
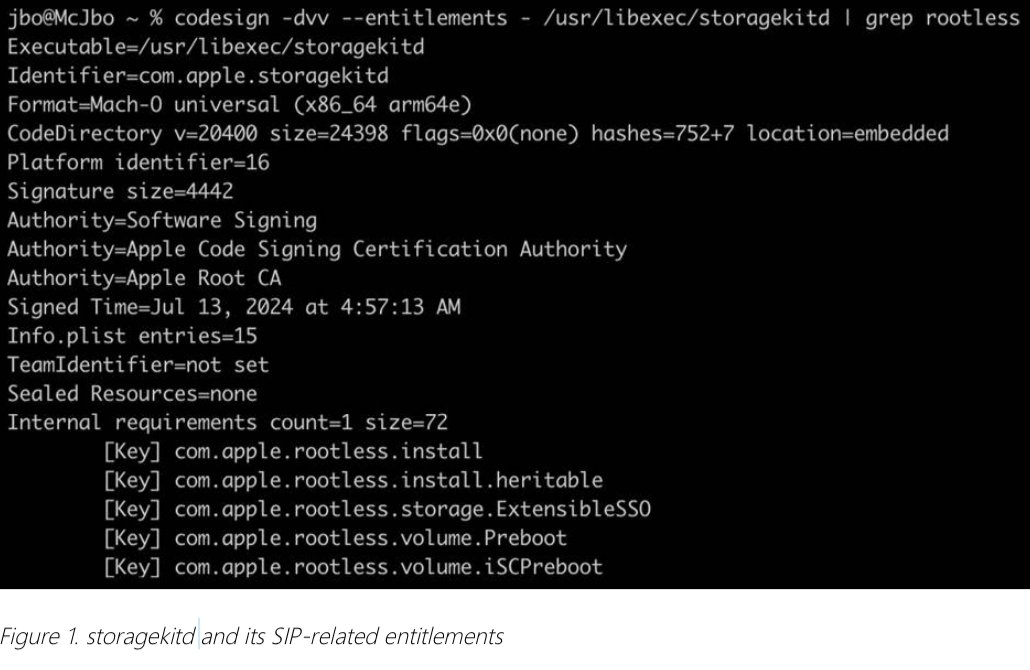
The vulnerability relies on “entitlements,” which are special permissions embedded in macOS processes. These entitlements are important to SIP as they govern what a process can and cannot do.
Some processes have private entitlements reserved for essential system functions, such as debugging or file management.
Microsoft researchers discovered that attackers could exploit entitled processes — specifically the storagekitd daemon, which manages disk state through Apple’s Storage Kit framework. Since storagekitd inherits broad privileges, it could spawn child processes capable of bypassing SIP.
Attackers could insert their own kernel extensions to gain control over the operating system without detection using the daemon.
After identifying the vulnerability, Microsoft disclosed it to Apple under its Coordinated Vulnerability Disclosure (CVD) process. Apple addressed CVE-2024-44243 in its December 11, 2024 security updates, urging all users to update their Macs immediately.
How to protect your Mac
The best way to protect your Mac from this vulnerability is to make sure it’s running the latest macOS update. Apple fixed the issue in its December 11, 2024, security patches, so it’s crucial to update if you haven’t already.
To check, head to System Settings > General > Software Update and install any available updates.
If you’re using an older Mac that doesn’t support the latest macOS, keep an eye on Apple’s security updates for patches that might still apply to your system. It’s also a good idea to avoid installing third-party kernel extensions unless you’re sure they come from a trusted source.
You won’t have to worry about accidentally disabling SIP. It’s enabled by default in macOS, and disabling it requires deliberate steps using Terminal in Recovery Mode.