Apple introduced a feature that would hide a user’s permanent MAC address in 2020, but it’s been virtually useless until iOS 17.1 thanks to a now patched vulnerability.
When a device connects to a network, it performs a necessary handshake, sharing its unique MAC address. If an entity can access the MAC addresses accessing networks at a large enough scale, they could track users as they move between networks.
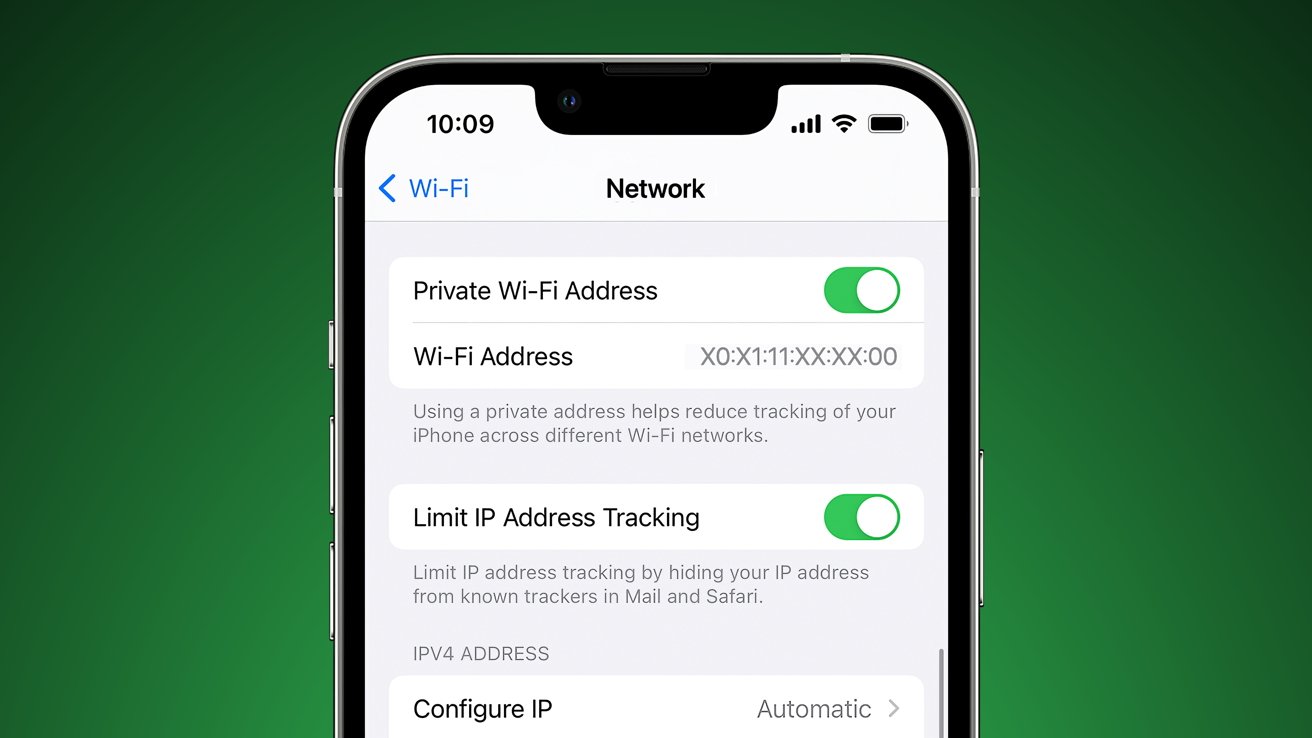
According to a report from Ars Technica, Apple implemented a feature that would prevent MAC address tracking, but a vulnerability has rendered it virtually useless since it debuted in iOS 14. The Private Wi-Fi Address feature is enabled by default and promises to assign a different MAC address to every unique SSID, which it did in practice.
The problem is the permanent MAC address that was supposedly being obfuscated by this feature was still being shared through port 5353/UDP. Basic MAC address sniffing was curtailed, but anyone looking could easily find the real MAC address, which presents a problem for those expecting this feature to work.
The report suggests that this would have been a simple fix, and it isn’t clear why Apple took three years to implement it. General users don’t need to worry about this vulnerability, but anyone who needed to hide their MAC address and expected the feature to work could have had their MAC address compromised.
Apple reports that the vulnerability has been patched in iOS 17.1. It was tracked as CVE02923-42846 and credited to Talal Haj Bakry and Tommy Mysk.




![9to5Rewards: MacBook Pro giveaway + Chargeasap Connect Pro 100W cable [Giveaway]](https://techtelegraph.co.uk/wp-content/uploads/2024/06/Jeffs-Studio-Setup-14-inch-MacBook-Pro-03-218x150.jpg)