CVE Trends was just warning us that over the past week the latest Apple vulnerability has racked up nearly 6 million audience interactions on Twitter.
CVE-2022-22620: 6M
CVE-2022-24086: 3.2M
CVE-2021-44521: 2.9M
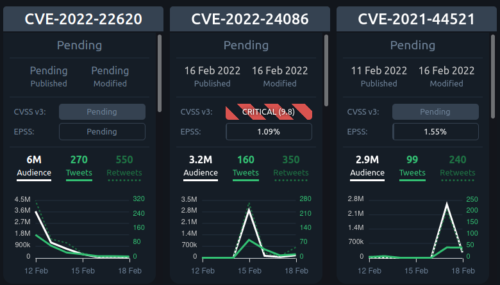
Very interesting to see such a long tail instead of the usual up and down audience curve.
Apple, per usual, is very tight-lipped about their emergency security patch, which has been credited to an anonymous researcher.
Impact: Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited. Description: A use after free issue was addressed with improved memory management.
Alleged so far is that this marks a 0-day in Apple devices (exploited in the wild before the patch was released), easily hacked by clicking on just one link (1-click) or perhaps even less (0-click through waterholing, XSS, MITM, captive portal, etc). It would be hard to allege anything higher risk.
It’s surely safe to say that releasing a 15.3.1 just two weeks after they announced ten major security fixes in the 15.3 release (including in-the-wild 0-day patch of CVE-2022-22587 — code execution with kernel privileges) means this minor version patch is even more unusually important.
Also worth noting is malware researchers pulling their “UPDATE NOW” alarm, and CISA saying “we’ve added one more” the next day after publishing their latest “Known Exploited Vulnerabilities Catalog”.
…evidence that threat actors are actively exploiting the vulnerability… remediation due date: 2/25/2022 [only two weeks from Apple’s patch release]
Highly unusual to have a critical patch announcement dropped almost immediately on top of a critical patch announcement. It doesn’t get any more serious than this one.
As a laugh I also have to give credit where due, since The Register apparently published on this vulnerability all the waaaay back in 1970.
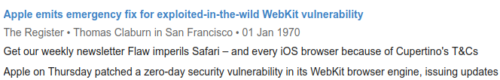
Leave it to a vulnerability reporting site to have an obvious integrity issue.
And as another laugh, that Register article cites a ex-Google program manager for Microsoft throwing stones from inside his glass house
Imagine, if you can, a world where installing an alternative browser as your default actually had a chance of protecting you from [a software company’s] shocking underinvestment in security
Indeed. Chrome on Google and Edge on Microsoft should be your last choice, given what we know about WebKit on Apple having issues.




