While Apple’s Advanced Data Protection drew backlash from the FBI, members of the infosec community agree it’s a step forward in user privacy and beneficial for enterprise security in an increasingly remote workforce.
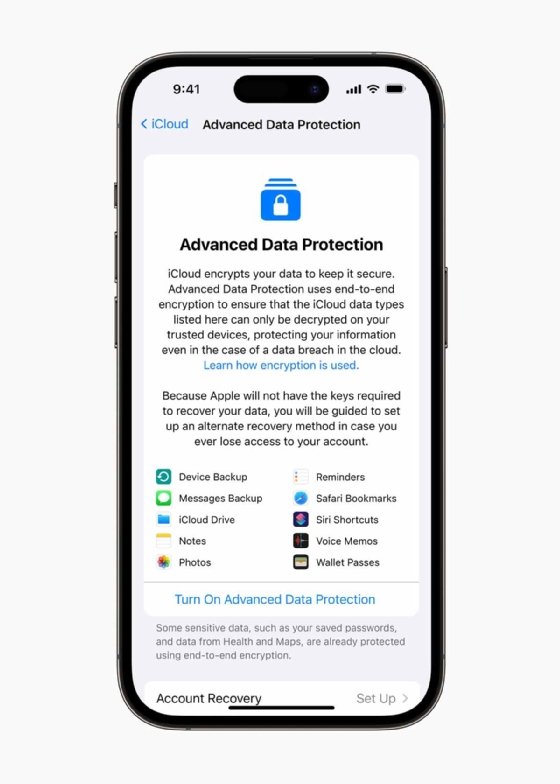
In December, Apple launched three new data security and authentication tools including iMessage Contact Key Verification, Security Keys for Apple ID and — most notably — Advanced Data Protection. The new offering expands Apple’s end-to-end encryption (E2EE) protection to the cloud, including device and messages backup, the iCloud drive, notes, photos, voice memos, wallet items and more.
With Apple’s encryption expansion, access to most cloud data will now be limited to users. Data recovery can only be achieved through passwords and recovery methods, and not even Apple can decrypt it. More significantly, the data will remain secure even if the cloud is breached, according to Apple.
Data breaches are an ongoing concern for consumers and enterprises alike. Even data that is stored in technology vendors’ clouds can be at risk. That issue was highlighted by a recent data breach at password manager LastPass, where threat actors stole both encrypted login credentials and unencrypted data such as website URLs.
By implementing Advanced Data Protection, which launched in the U.S. and will being rolling out to worldwide users in early 2023, the number of E2EE categories rises from 14 to 23. However, upgrading to iOS 16.2 or later is required.
The launch was roundly praised by encryption experts and privacy advocacy groups such The Electronic Frontier Foundation (EFF) and Access Now. Users that opt into Advanced Data Protection for iCloud “will be protected even if there is a data breach in the cloud, a government demand, or a breach from within Apple (such as a rogue employee),” said Joe Mullin, a policy analyst at EFF, in a blog post.
Andry Laremenko, co-founder and CTO of Israeli infosec startup Hub Security, told TechTarget Editorial the move continues a big industry trend he’s observed: full privacy and giving the control of user data to the user. Therefore, he believes it will be a big selling point for both consumers and businesses.
Apple is a significant enterprise player, and companies that provide E2EE remove the risk of attackers stealing user data from the company server, he said. Data breaches, particularly those that stem from a ransomware attack, pose significant problems. Especially if that data belongs to hospitals, schools, and critical infrastructures.
“It’s also about the company bottom line. If the information on company servers is encrypted, even if hackers breach and steal everything, it’s all encrypted. The company will not get fined, get a bad reputation or lose money,” Laremenko said.
For both consumers and businesses, Advanced Data Protection will be important with the move to remote work. Jack Poller, senior analyst at Enterprise Strategy Group, told TechTarget Editorial that E2EE provides users with the same level of protection as is standard for the corporate world. Additionally, Geoff Cairns, an analyst at Forrester Research, noted how useful it will be to users that are deemed high-value targets by threat actors.
Securing consumer’s personal devices, such as iPhones or MacBooks, that may contain sensitive enterprise data is a growing focus.
“When everyone’s working remotely, then the cloud infrastructure becomes more open to the internet — to hackers — and everyone connects to the internet. It’s much more exposed,” Laremenko said. “Apple is now locking this up from the user perspective.”
Users beware
Now that the root of trust lays in users’ hands, holding onto the encryption keys is vital. If something is lost, such as important photos or messages, Apple will no longer be responsible. Both Cairns and Laremenko worry this could present a problem for some users.
Cairns, who specializes in identity and access management for enterprises, is interested to see how key management evolves following the full roll out of Advanced Data Protection. Key management has always been difficult when it comes to encryption, he said.
Laremenko went as far as to call it a disadvantage for the user side because no one else can restore the lost data. He recommended that users test the recovery procedure periodically.
“They need to change their state of mind, because now they are the sole owners and protectors of their entire history,” Laremenko said.
Additionally, Nick DeLena, partner at PFK O’Connor Davies, which specializes in cybersecurity and privacy, warned that users should be aware that iCloud mail, contacts and calendars are not included in the protected data categories. Because Apple still holds the keys, particularly in the case of email, he emphasized that iCloud mail should not be considered as secure as encrypted email services such as ProtonMail.
More importantly, Advanced Data Protection does not guarantee sensitive data won’t be compromised. The main concern goes back to proper cybersecurity hygiene for the user.
“End-to-end encryption does not protect the user against poor password hygiene. So if someone were to gain access to one of your trusted devices, they would be able to read the encrypted content of your iCloud account,” DeLena said.
Backlash by law enforcement
While infosec and privacy experts applauded Apple’s encryption move, the FBI expressed concerns that it would interfere with law enforcement actions related to cyber attacks, drug trafficking and terrorism.
Dustin Volz, cybersecurity and intelligence reporter for the Wall Street Journal, shared the FBI’s response to Apple’s Advanced Data Protection launch in a Twitter post. The FBI issued the statement on Dec. 7, the same day it was announced by Apple.
“End-to-end and user-only access encryption erodes law enforcement’s ability to combat these threats and administer justice for the American people,” the statement read.
Without the keys, Apple cannot assist law enforcement with accessing the encrypted iCloud data, even if subpoenaed. DeLena noted how encryption has been an ongoing contentious issue, heightened by the San Bernardino shooting in 2015 after Apple refused to assist the FBI in hacking into the shooter’s phone.
DeLena also found the FBI’s claims about E2EE to be ironic.
“Any backdoors or weaknesses built into encryption technologies are inherently compromising the security of that encryption. The same backdoor used by law enforcement can, in theory, be exploited by a hacker,” DeLena said in an email to TechTarget Editorial.
In addition to rolling out E2EE for back-ups, Apple also canceled its controversial plan to implement client-side scanning of iCloud Photos for child sexual abuse material (CSAM), which was proposed in 2021. Instead, photos will be more secure with E2EE, which Poller said will protect user privacy and remove the potential for surveillance.
Access Now applauded both moves, calling them a “welcome brick in people’s online privacy and security wall” and encouraging other technology, particularly cloud storage and communications providers, to follow Apple’s lead.



