
Scams like phishing and social engineering are continuing to grow with some specifically targeting Apple users. With that in mind, Apple has shared a new support document with official tips on how to protect your Apple ID and other online accounts, how to spot and report scam emails, calls, and more.
We’ve seen a few different scams recently aimed at Apple users with a “smishing” iCloud link attack being the latest.
As it happens, Apple has shared a new support document on how to protect your account, avoid phishing, social engineering, scam calls, and more.
Along with being a valuable refresher for everyone, this is a great resource to share with less tech-savvy family and friends.
Apple’s advice on how to protect your Apple ID and avoid scams
Protecting your Apple account
Here are Apple’s 8 tips to make your Apple ID as secure as possible:
- Never share personal data or security information like passwords or security codes, and never agree to enter them into a webpage that someone directs you to.
- Protect your Apple ID. Use two-factor authentication, always keep your contact information secure and up to date, and never share your Apple ID password or verification codes with anyone. Apple never asks for this information to provide support.
- Never use Apple Gift Cards to make payments to other people.
- Learn how to identify legitimate Apple emails about your App Store or iTunes Store purchases. If you send or receive money with Apple Cash (U.S. only), treat it like any other private transaction.
- Learn how to keep your Apple devices and data secure.
- Download software only from sources you can trust.
- Don’t follow links or open or save attachments in suspicious or unsolicited messages.
- Don’t answer suspicious phone calls or messages claiming to be from Apple. Instead, contact Apple directly through our official support channels.
Apple also has a dedicated support document on getting help with security if you run into trouble with passwords/purchases, lost or stolen products, personal safety, and more.
How to handle suspicious emails, messages, and calls

- If you receive a suspicious email that looks like it’s supposed to be from Apple, please forward it to reportphishing@apple.com.
- If you receive a suspicious FaceTime call (for example, from what looks like a bank or financial institution), email a screenshot of the call information to reportfacetimefraud@apple.com. To find the call information, open FaceTime and tap the More Info button “i” next to the suspicious call.
- If you receive a suspicious link to a FaceTime call in Messages or Mail, email a screenshot of the link to reportfacetimefraud@apple.com. The screenshot should include the phone number or email address that sent the link.
- To report a suspicious SMS text message that looks like it’s supposed to be from Apple, take a screenshot of the message and email the screenshot to reportphishing@apple.com.
- To report spam that you receive in your iCloud.com, me.com, or mac.com Inbox, mark the spam emails as Junk or move them to your iCloud Junk folder. When you mark an email as junk, you help improve iCloud Mail filtering and reduce future spam.
- To report harassment, impersonation, or other types of abuse that you receive in your iCloud.com, me.com, or mac.com Inbox, send them to abuse@icloud.com.
- To report spam or other suspicious messages that you receive through Messages, tap Report Junk under the message. You can also block unwanted messages and calls.
- Report scam phone calls to the Federal Trade Commission (U.S. only) at reportfraud.ftc.gov or to your local law enforcement agency.
How to catch social engineering, phishing, and other scams
Social engineering attackers use impersonation and manipulation to first gain your confidence and trust. Then, they trick you into handing over sensitive data or providing them with access to your account information. They use a variety of tactics to impersonate a trusted company, entity, or someone that you know.
Watch for these signs to help identify if you’re being targeted as part of a social engineering attack:
- A scammer may call you from what appears to be a legitimate phone number for Apple or another trusted company. This is called “spoofing.” If the call seems suspicious, consider hanging up and dialing the vetted number for the company yourself.
- Scammers often mention personal information about you in an attempt to build trust and seem legitimate. They may refer to information that you consider private, such as your home address, place of employment, or even your Social Security number.
- They will often convey a desire to help you resolve an immediate problem. For example, they may claim that someone broke into your iPhone or iCloud account, or made unauthorized charges using Apple Pay. The scammer will claim they want to help you stop the attacker or reverse the charges.
- The scammer usually creates a strong sense of urgency to avoid giving you time to think and to dissuade you from contacting Apple yourself, directly. For example, the scammer may say that you’re free to call Apple back, but the fraudulent activities will continue and you will be liable. This is false, and designed to prevent you from hanging up.
- Eventually scammers will request your account information or security codes. Typically they will send you to a fake website that looks like a real Apple sign-in page and insist that you verify your identity. Apple will never ask you to log in to any website, or to tap Accept in the two-factor authentication dialog, or to provide your password, device passcode, or two-factor authentication code or to enter it into any website.
- Sometimes, scammers will ask you to disable security features like two-factor authentication or Stolen Device Protection. They will claim that this is necessary to help stop an attack or to allow you to regain control of your account. However, they are trying to trick you into lowering your security so that they can carry out their own attack. Apple will never ask you to disable any security feature on your device or on your account.
How to catch scam texts and emails
Scammers try to copy email and text messages from legitimate companies to trick you into giving them your personal information and passwords. These signs can help you identify phishing emails:
- The sender’s email or phone doesn’t match the name of the company that it claims to be from.
- The email or phone they used to contact you is different from the one that you gave that company.
- A link in a message looks right, but the URL doesn’t match the company’s website.
- The message looks significantly different from other messages that you’ve received from the company.
- The message requests personal information, like a credit card number or account password.
- The message is unsolicited and contains an attachment.
Downloading apps
Apple also warns about downloading software, highlighting that the safest way to install apps is through its official App Store or directly from a developer’s website.
Apple ID password reset attack
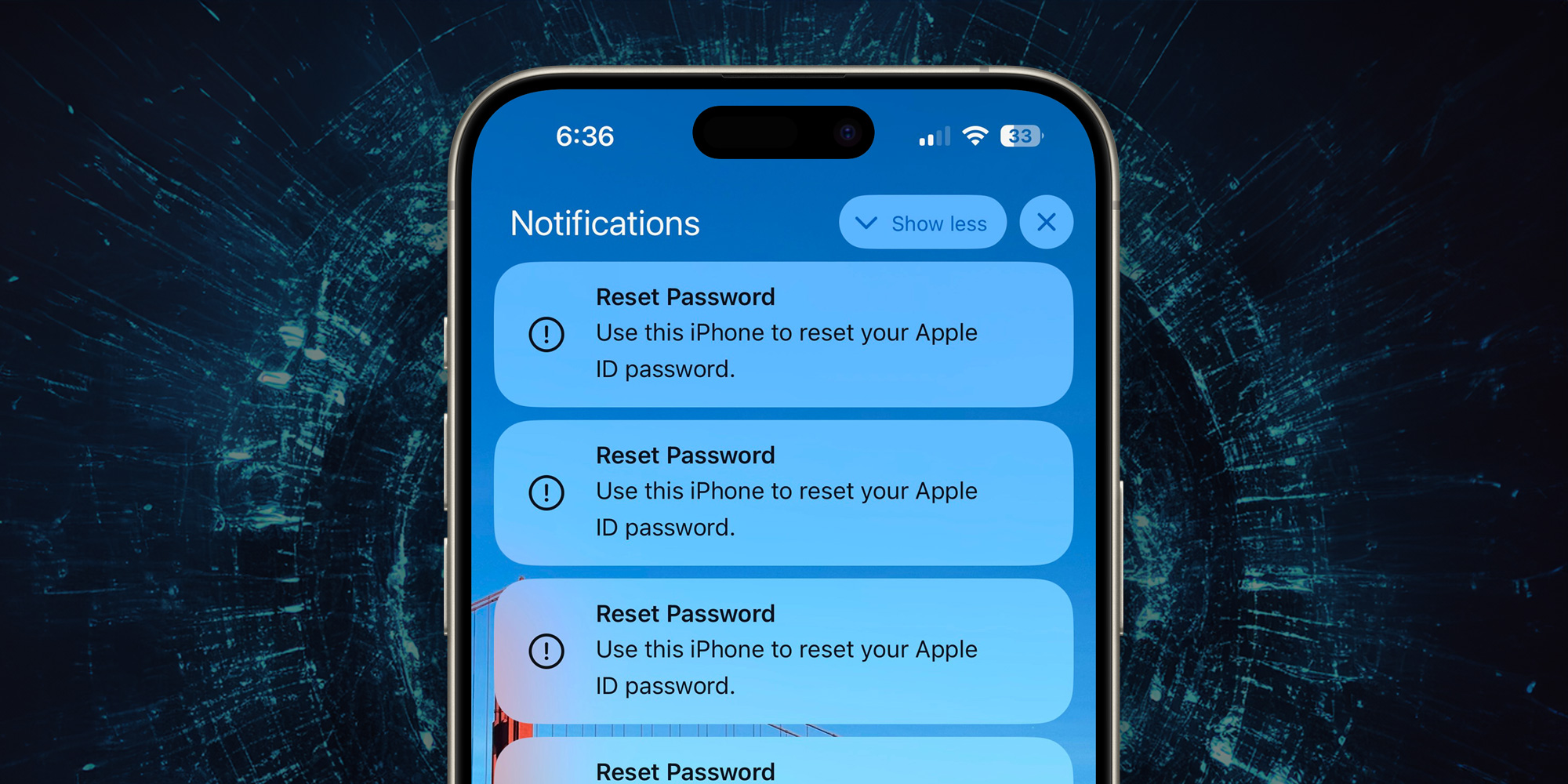
One recent scam that Apple didn’t cover in this support document is the Apple ID password reset attack that resurfaced this year.
We’ve got a full explainer on how to handle that:
Have you been seeing more scams this year? Share your experience in the comments!
FTC: We use income earning auto affiliate links. More.




