Windows Defender, built into Windows 11, eliminates the need for a third-party security app. While the default Windows Defender settings are sufficient for most situations, I’ve made these five changes to the Windows Defender settings for optimal security.
1 Core Isolation
Core isolation has been part of the Windows ecosystem since Windows 10 and uses virtualization-based security (VBS) to protect your computer from malicious actors. VBS and core isolation ensure that all important processes on your computer run in a virtualized environment, isolated from other processes on your system. This prevents malicious actors from interfering with these processes and making your computer unstable, even if it gets infected by a virus or malware.
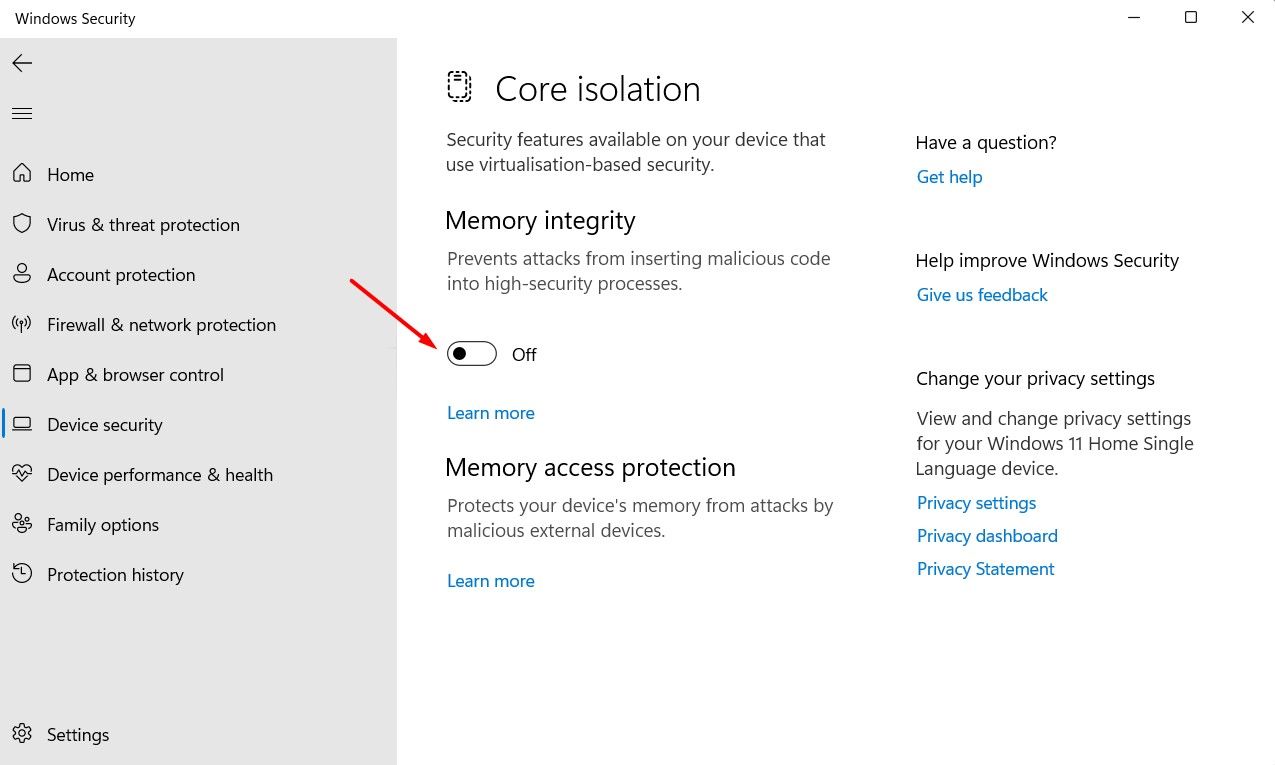
Under core isolation, there’s an important feature called memory integrity, also known as Hypervisor-protected Code Integrity (HVCI). This feature prevents threats from interfering with processes that have low-level access to the Windows kernel by isolating them from malicious actors.
The memory integrity feature is typically enabled on most computers, but on some, it might be disabled, and it can also be turned off after installing a Windows update. You should enable it to ensure the important processes on your computer are protected from threats.
To enable it, open the Windows Security app, choose “Device Security” from the left sidebar, click on “Core Isolation Details,” and then toggle on “Memory Integrity.” Click “Yes” when prompted by the User Account Control (UAC).
Afterward, restart your computer, and memory integrity will start protecting the important processes on your computer.
2 Smart App Control
Smart App Control is one of the recently introduced security features in Windows 11. It blocks apps that might affect your device’s performance, display unexpected ads, install extra software you didn’t ask for, or perform other actions that weren’t expected from that app.
What sets this feature apart from other security features is that it assesses whether an app can be trusted to run on your computer based on 43 trillion signals gathered daily. It uses artificial intelligence to keep its security model up-to-date, ensuring it blocks unknown apps often associated with malware.
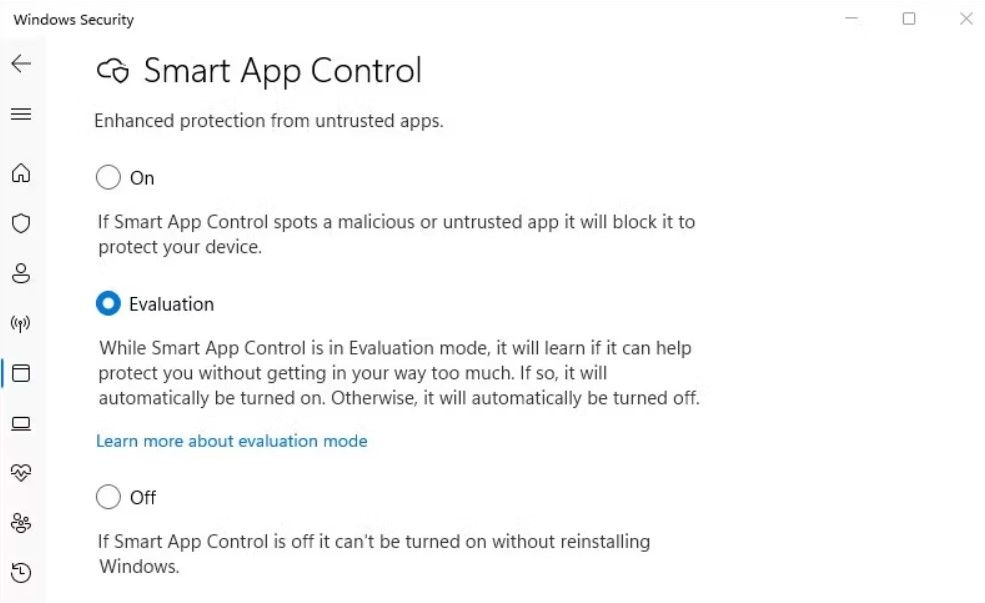
The best part about this feature is its ability to intelligently decide when to block apps or when to stay out of the way. If it detects that your usage involves installing a lot of unknown or experimental apps, it won’t interfere. It accomplishes this by running in evaluation mode for a period when you first start using the feature. During this time, it monitors the apps you use to determine if the feature is necessary for you or if it would disrupt your workflow by blocking apps you use regularly.
If it concludes that you install many unknown apps daily, the feature will be turned off. However, if it finds that it can help without being too intrusive, it will remain enabled.
When Windows 11 is first installed on your computer, this feature will automatically start in evaluation mode. While it will eventually decide whether you need the feature, you can manually enable or disable it at any time. To do this, open the Windows Security app, navigate to App & Browser Control > Smart App Control Settings, and choose whether to enable or disable the feature.
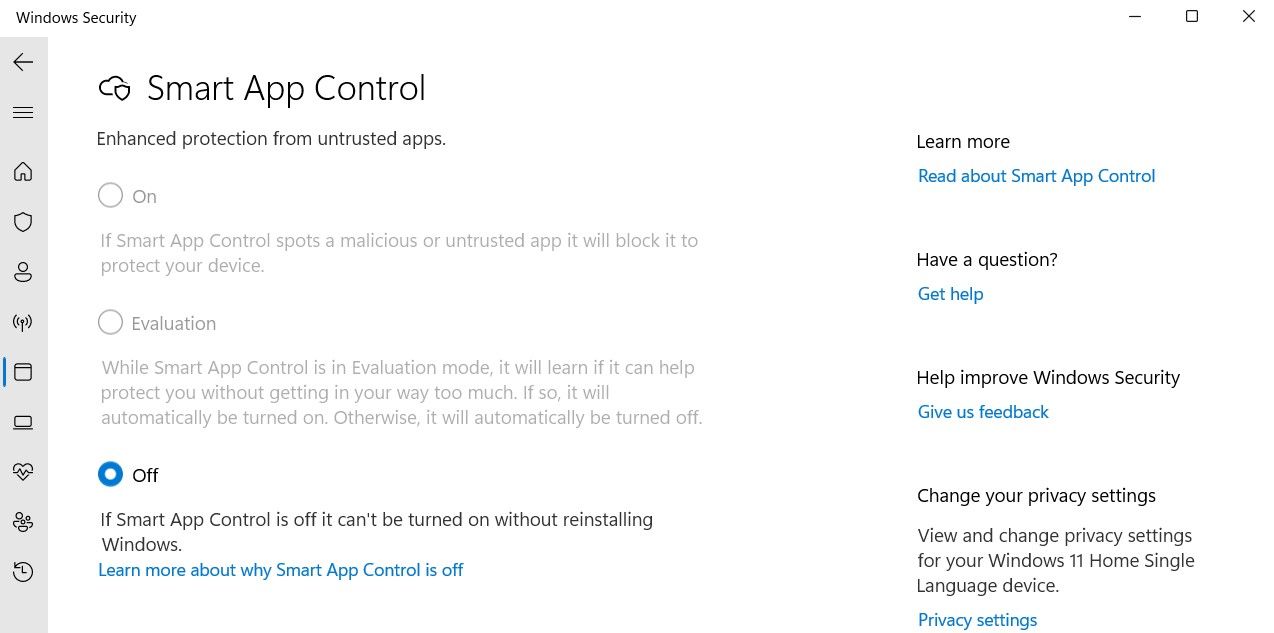
If you find that Smart App Control is already set to off, it means that after evaluating your usage, the feature has decided it’s not necessary for you.
However, if you change how you use your computer—such as installing fewer apps—you can turn it back on. In this case, you will need to perform a clean installation of Windows 11, after which this feature will again start in evaluation mode, evaluate your usage, and decide whether to keep the feature enabled or disabled.
3 Controlled Folder Access
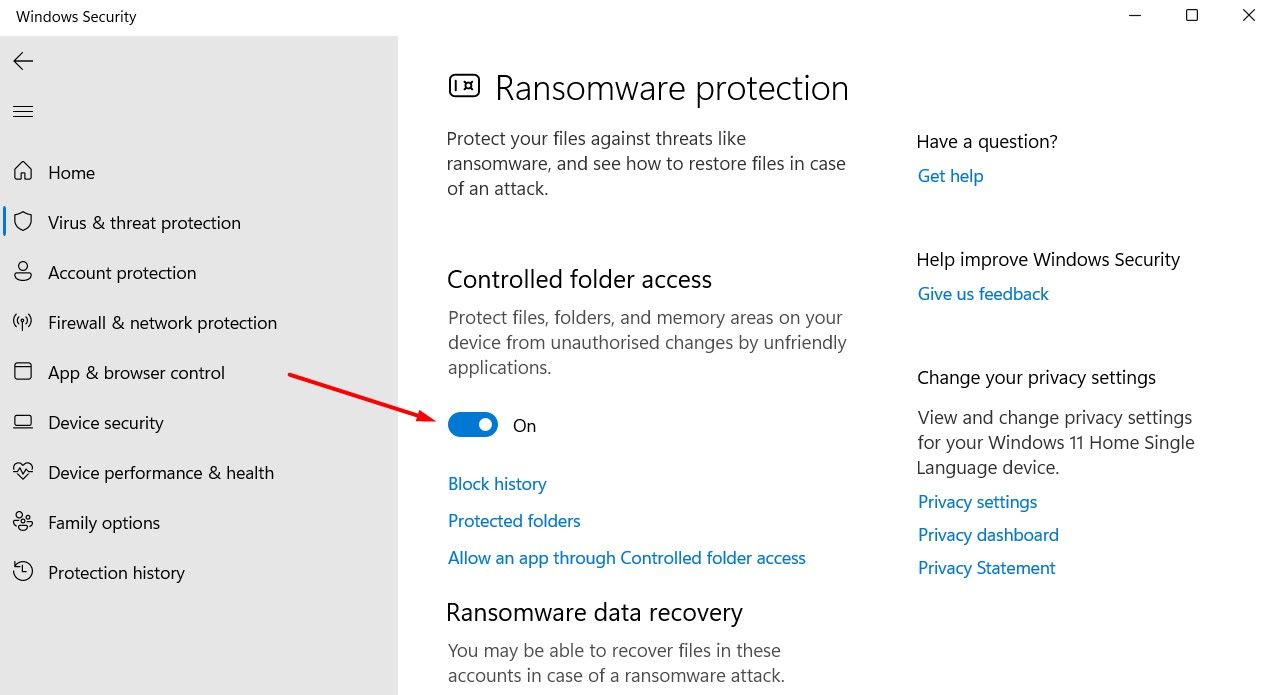
Controlled Folder Access is a ransomware protection feature from Windows that ensures your files can’t be locked up and held for ransom by malicious software. This feature protects important folders on your computer, such as Documents, Pictures, Music, and Videos, from malicious actors, making it difficult for them to tamper with the content. Only trusted applications are allowed to modify files in these protected folders.
Once Controlled Folder Access is enabled, you will receive a notification if it blocks a program attempting to access a protected folder. You might see this notification frequently if you play PC games, as many games save their files in the Documents folder, which is protected under this feature.
The good news is that you can manually add folders you want to protect with Controlled Folder Access. Additionally, if a program is blocked but you believe it is safe, you can manually allow it through this feature.
To enable Controlled Folder Access, open the Windows Security app and navigate to Virus & Threat Protection > Manage Ransomware Protection. Then, toggle on “Controlled Folder Access.”
4 Dynamic Lock
It’s quite common to step away from your computer for a few seconds, and then an urgent task comes up, causing you to leave home without turning off your computer. In such cases, your computer remains open and vulnerable to unauthorized access. To address this issue, you can use the Dynamic Lock feature in Windows 11.
The Dynamic Lock feature automatically locks your Windows computer when the signal from a paired Bluetooth device, such as your smartphone, drops below the maximum Received Signal Strength Indicator (RSSI) value. The signal threshold varies depending on the Bluetooth version. For example, Bluetooth version 5 has a range of up to 800 feet. However, walls, furniture, and other physical obstructions can interfere with the signal and reduce its range.
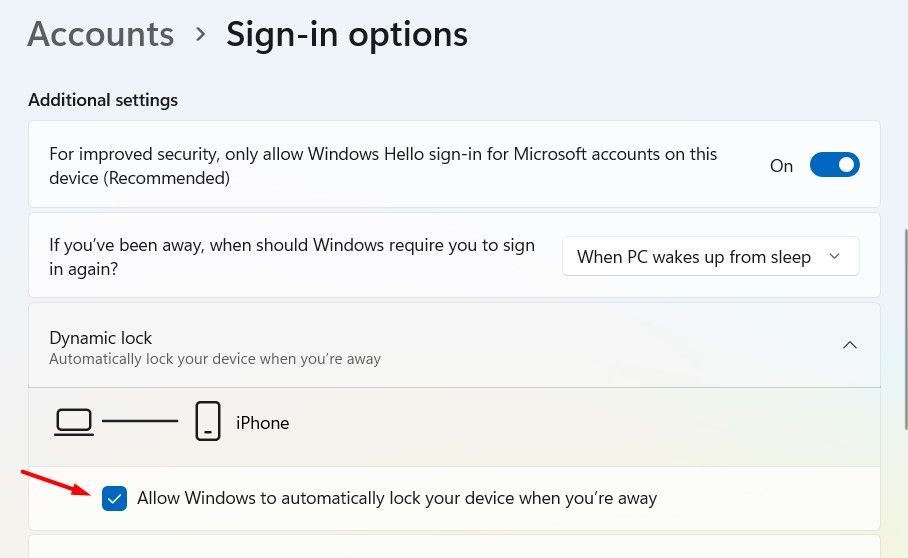
To use Dynamic Lock, first connect your smartphone or any Bluetooth-enabled device to your computer via Bluetooth. Then, open the Settings app, click on “Accounts,” select “Sign-in Options,” choose “Dynamic Lock,” and check the option that says “Allow Windows to automatically lock your device when you’re away.”
Once connected, you will see the name of the Bluetooth device paired with your computer. Your computer will automatically lock when you take the Bluetooth device out of range.
However, it’s important to note that this feature only works if the Bluetooth signal drops and your computer is idle. If someone gains access to your computer before the Bluetooth signal weakens, the device won’t lock. Therefore, the Dynamic Lock feature reduces the likelihood of unauthorized access if you forget to lock your computer, but it doesn’t fully replace the need to lock it when leaving your device unattended.
5 Reputation-Based Protection
Reputation-based protection is another important setting in the Windows Security app that helps prevent the installation of potentially unwanted applications (PUAs). When installing third-party applications, you may notice that the application you’re trying to install attempts to include additional software, such as browser extensions or other programs, which could be malware or crypto miners.
To avoid this, you must be cautious with checkboxes during the installation process. However, with reputation-based protection enabled, you can install applications without worrying about such risks. This feature will detect PUAs attempting to install and send you an alert, allowing you to choose whether to allow or block the application.
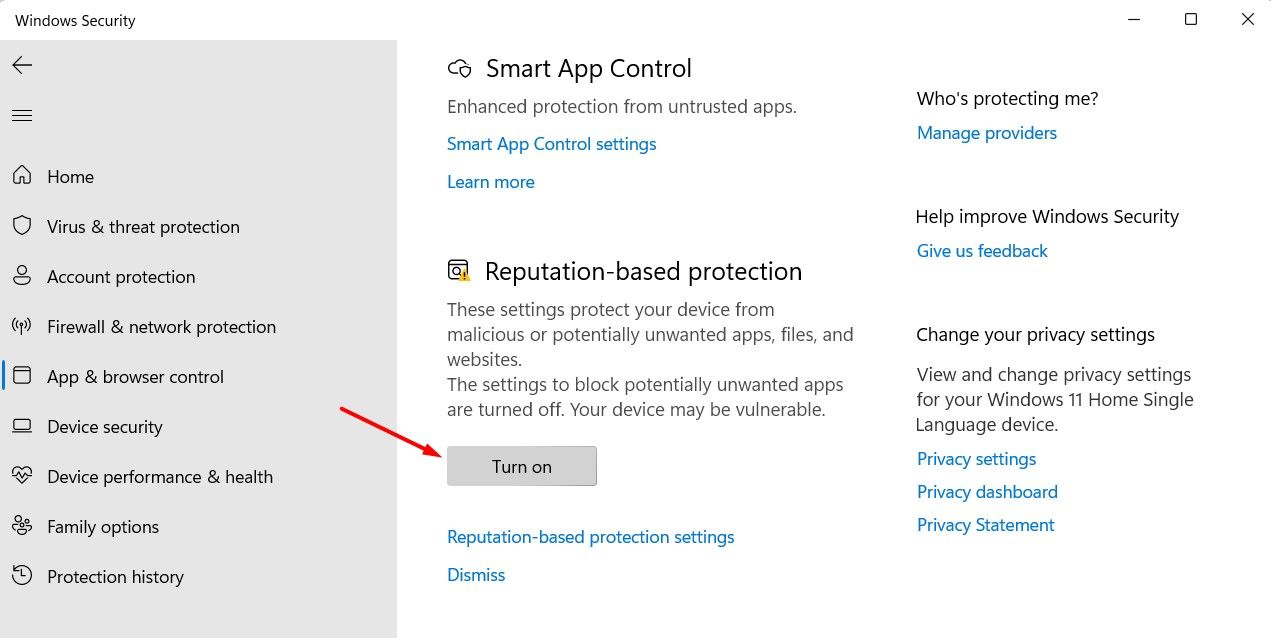
To enable reputation-based protection, open the Windows Secuirty app, select “App & Browser Control” from the left sidebar, and click the “Turn On” option under Reputation-based protection.
These are some important Windows security app settings you must configure to keep your computer safe. However, even with these settings enabled, malicious actors may still find new ways to attack your computer. That’s why it’s crucial to be cautious when interacting with untrusted links on the internet and be very careful when receiving files on your device from various sources.