Commercial VPNs’ primary mission has traditionally been to protect user privacy online, but over the years they’ve expanded their offerings to include many more “convenience” features. Here, I’ll outline the VPN features I consider critical. I will not sign up for a VPN provider that doesn’t support these.
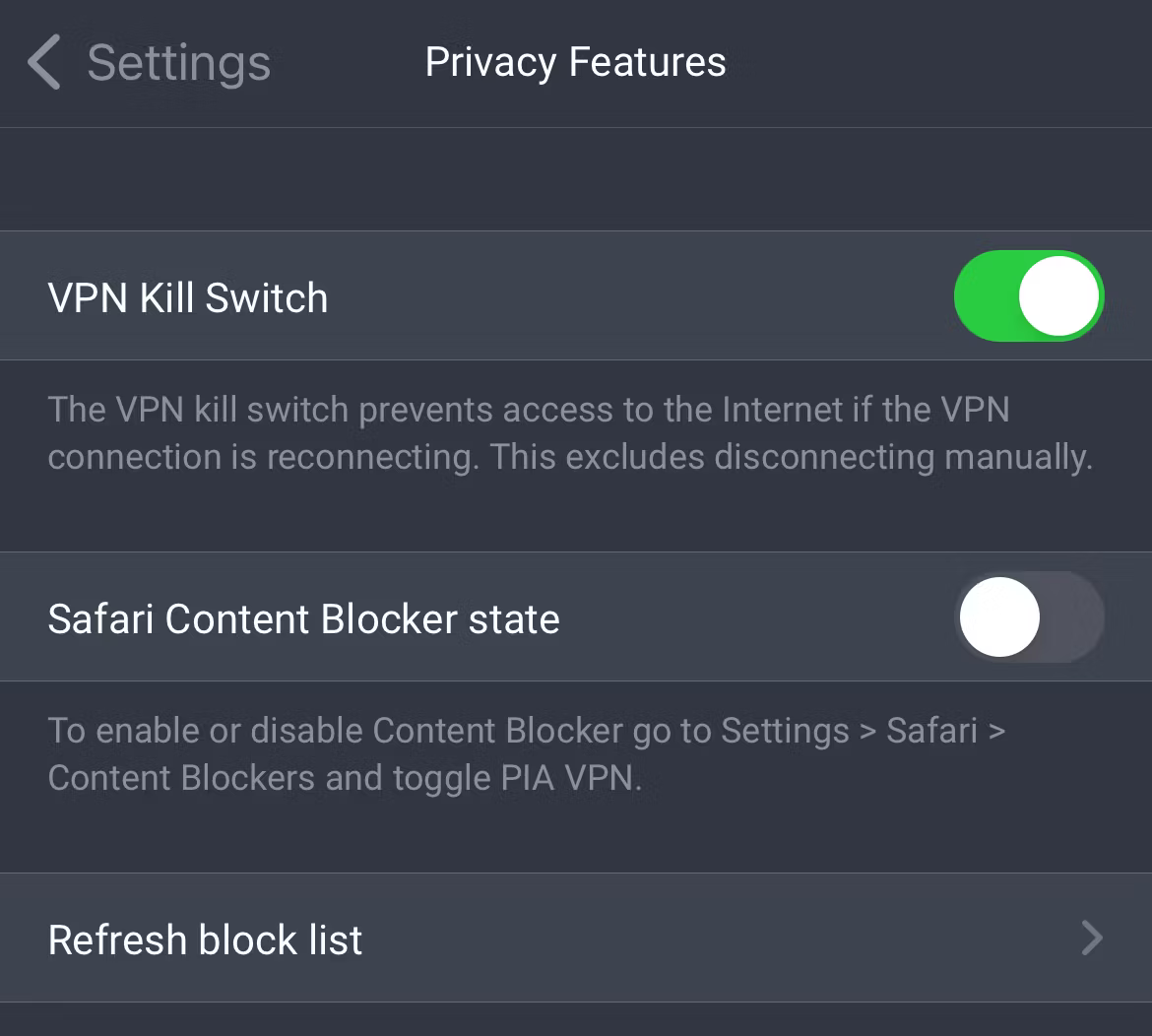
1 A Kill Switch
When you’re on VPN, your traffic is encrypted, and your IP address is swapped out for the VPN server’s IP address. That enables you to spoof your location while making it harder to identify you.
But what happens if your VPN connection drops for any reason? Your traffic will start flowing out of your ISP connection, using the ISP-assigned IP address that can be traced back to you.
A kill switch is designed to prevent that scenario. With the kill switch enabled in your VPN app, if your connection drops, the kill switch kicks in, and all traffic is blocked until you reconnect to the VPN.
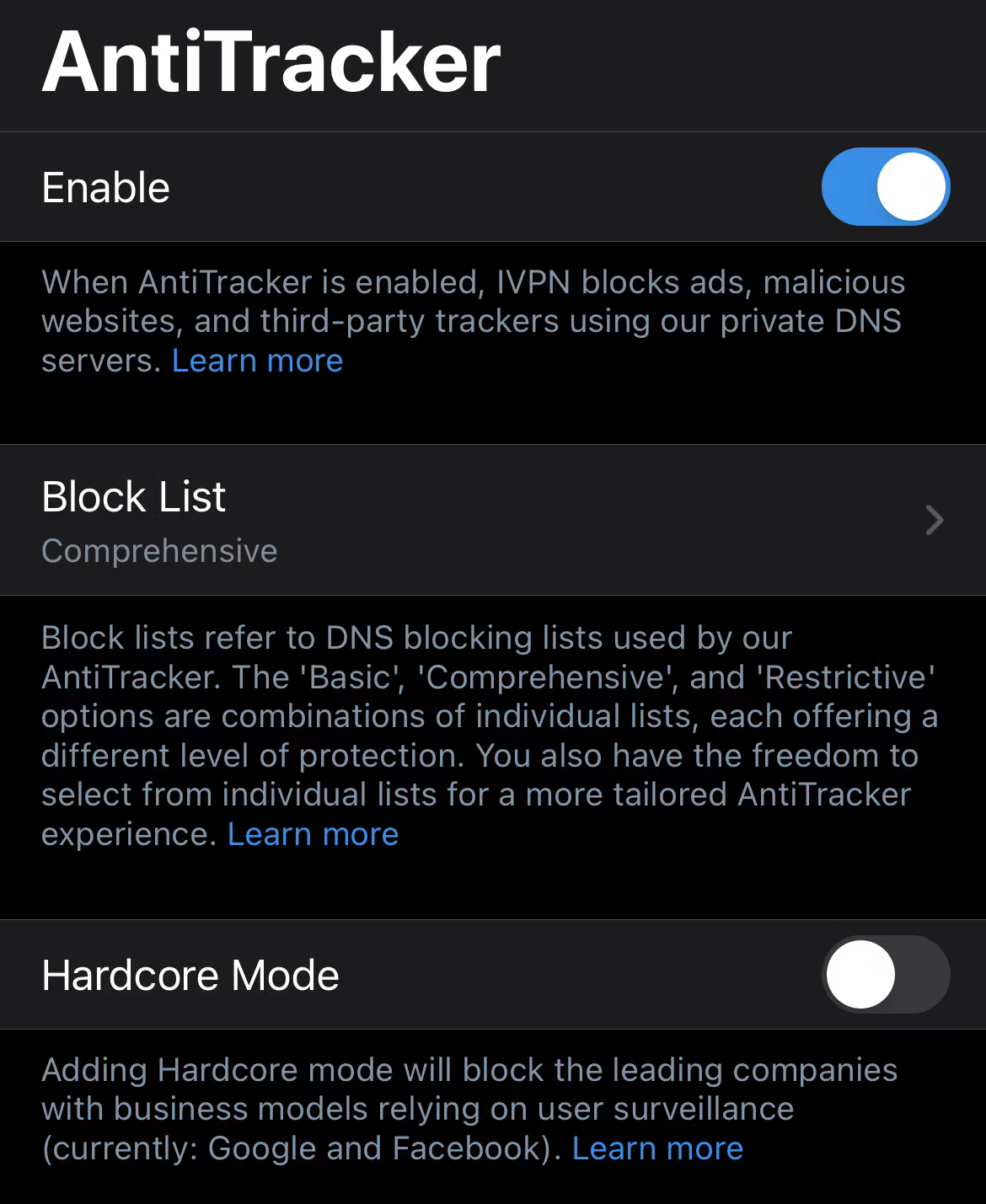
2 A Tracker Blocker
The internet can be a hostile place, with no shortage of entities looking for a piece of your data. Hence, the web is full of trackers, scripts, and ads that funnel as much information about you as possible to marketing companies, data brokers, governments, or malicious actors.
Using a tracker blocker while using a VPN significantly enhances user privacy. Tracker blockers come in all shapes and sizes. You may have one installed as an extension in your browser. VPN providers tend to block trackers using DNS blocklists.
Whenever you access a URL, your request is first sent to your Domain Name Server (DNS), which translates the URL to its IP address (i.e., 198.243.72.116) to enable the connection. With an active DNS blocklist, when your requests are sent to DNS, the requested IP address (or domain) is referenced against the blocklist. If there’s a match, the request is blocked. If not, your traffic is allowed on its way.
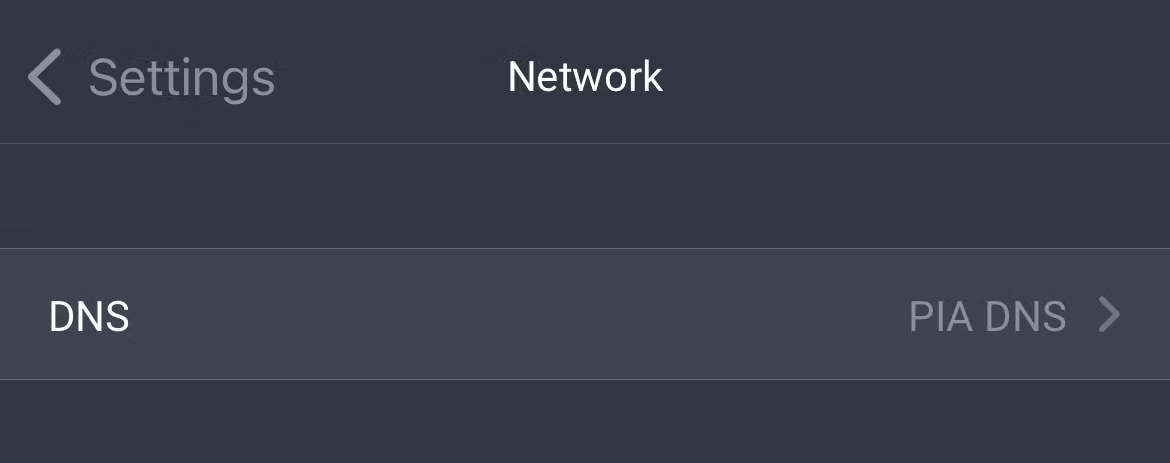
3 In-Tunnel DNS
While on the subject of DNS, a reputable VPN will provide in-tunnel DNS. When you connect to a VPN, you create a tunnel that encrypts all traffic between you and the VPN server.
With in-tunnel DNS, your DNS server is replaced by the VPN provider’s DNS server, which is only accessible inside the encrypted VPN tunnel.
This approach has two main benefits:
- Your DNS queries are not sent to either your ISP or a third party. They stay within your trusted VPN provider’s network.
- Your DNS requests are protected by the VPN’s encryption. So, even if you’re not using (explicitly) encrypted DNS (DNS over TLS or DNS over HTTPS), your DNS traffic will still benefit from the VPN’s encryption, keeping your DNS requests as private as the rest of your traffic.
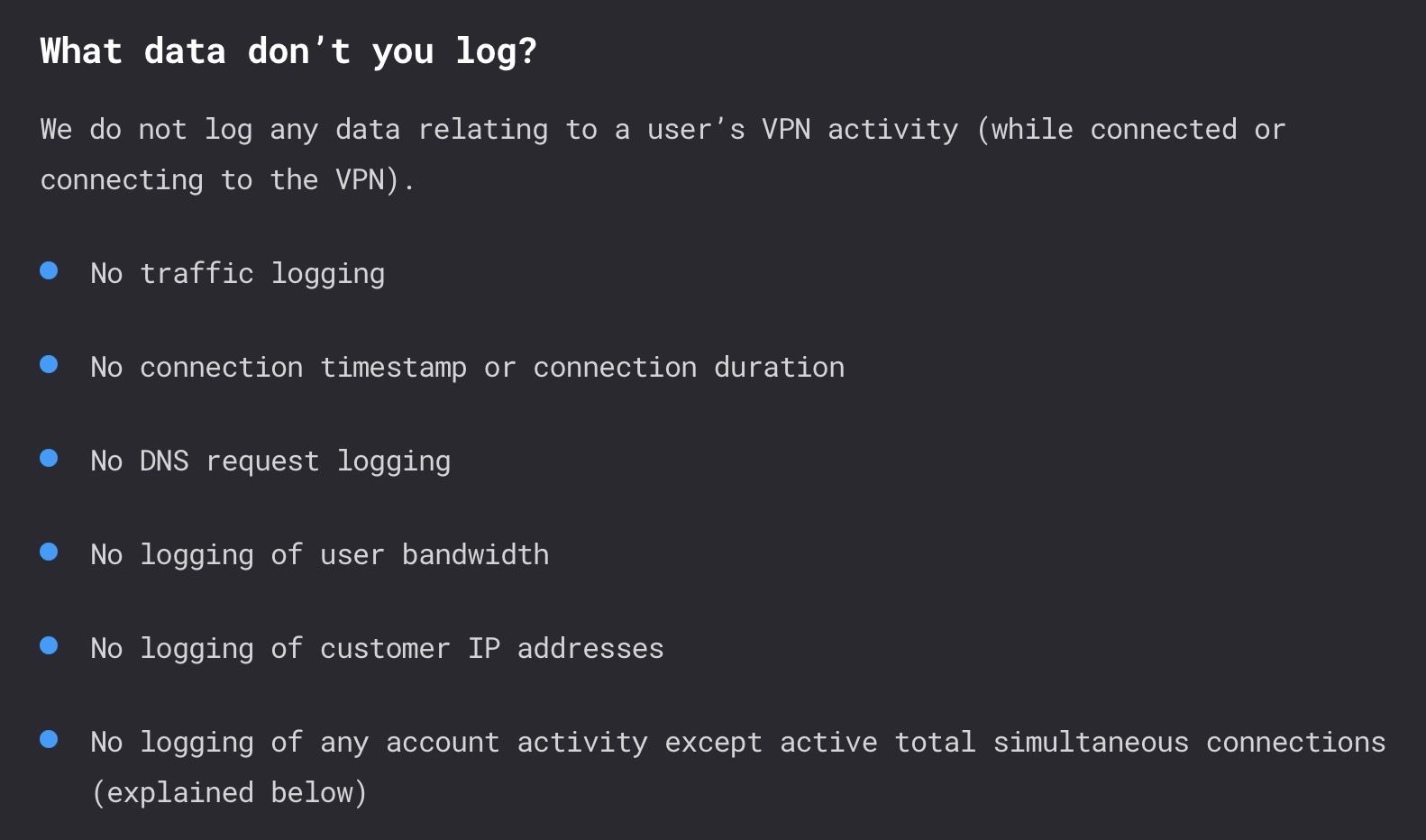
4 A Clear and Transparent No-Logging / Privacy Policy
If you’re going to use a commercial VPN, you will have to trust your VPN provider. Because all of your traffic is being proxied through your VPN provider’s network, it has the technical ability to see everything you’re doing online.
That’s where a provider’s privacy policy comes into play. A VPN provider’s privacy policy should clearly lay out what it collects, why, and what it doesn’t collect.
Ideally, the provider won’t simply print a promise in its privacy policy. Many reputable commercial VPN providers take technical measures to either disable logging on their network or erase all logs as they get collected.
5 Support for Simultaneous Connections
I take my online privacy seriously. I also have many devices, and I wouldn’t want to purchase multiple subscriptions to protect all of them. So, I tend to look for providers that support a good number of simultaneous connections.
In the past, many VPN providers capped the number of simultaneous connections at five. Today, given how connected devices have become staples of modern life, most providers have upped this to ten simultaneous connections—with some even offering unlimited simultaneous connections.
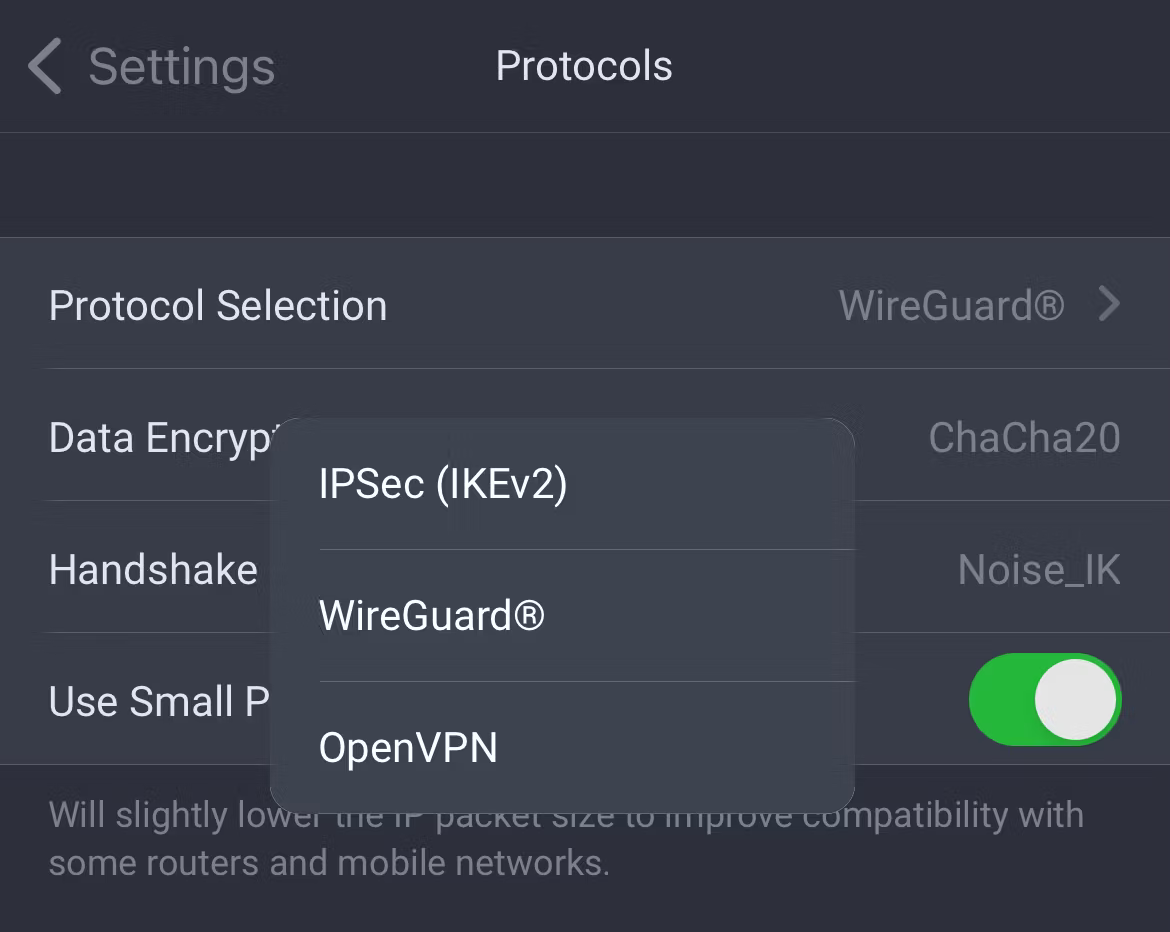
6 Open-Source Protocols and Encryption Algorithms
Encryption is the crux of any VPN service. A VPN is only as good as its encryption, and that comes down to the VPN provider’s supported VPN protocols and encryption algorithms.
A reputable provider should only support open-source VPN protocols. That’s because only open-source code can be reviewed by security researchers to ensure it does what it says on the tin. Proprietary code can’t be reviewed, so you’re left having to cross your fingers that whoever wrote the code did a good job. The same goes for encryption algorithms.
The open-source VPN protocols that VPN providers should support are:
While PPTP and L2TP/IPsec are open-source protocols, they’re deprecated and should no longer be used. So keep an eye out for those.
The open-source encryption algorithms that VPN providers should support are:
There are others, but the above are the most commonly used.
We each have our own tolerance levels to risk and our own priorities when it comes to safeguarding our data. The six points here make it clear what mine are, but your list could be different without being “wrong.”