 Source: Daniel Rubino / Windows Central
Source: Daniel Rubino / Windows Central
Microsoft is once again sounding the alarm so that you, the user, stay informed about the latest malware campaigns and cyber threats. This time, the alert is for Tarrask, a “defense evasion malware” that uses Windows Task Scheduler to hide a device’s compromised status from itself.
The attack comes from Hafnium, the state-sponsored, China-based group that you may recall to be a big deal because of its involvement in the Microsoft Exchange meltdown of 2021. The data gathered during that ordeal has been speculated to be fuel for AI innovations by the Chinese government.
Microsoft is currently tracking Hafnium’s activity when it comes to novel exploits of the Windows subsystem. Hafnium is using Tarrask malware to ensure that compromised PCs remain vulnerable, employing a Windows Task Scheduler bug to clean up trails and make sure that on-disk artifacts of Tarrask’s activities don’t stick around to reveal what’s going on.
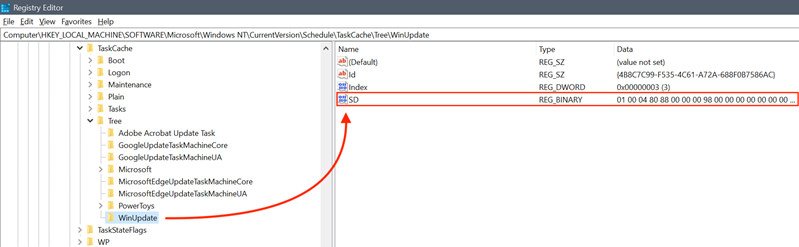
Microsoft has high-level recommendations for how to combat Tarrask, which you can check out at the company’s blog post on the subject (via BleepingComputer). Cyber resistance guidance in this case includes modifying audit policies, checking for scheduled tasks without SD (security descriptor) values, and more.
If you find these sorts of Microsoft PSAs to be useful, be sure to check out the company’s security summit on May 12, wherein it will explore the latest cybersecurity threats in-depth and give you a chance to ask Redmond’s in-house experts questions live.
We may earn a commission for purchases using our links. Learn more.




