A new phishing attack going after Mac users has been discovered, one that changed tactic only after the previously targeted Windows users received an Edge browser update.
Phishing attacks are quite common threats for people to deal with, as online criminals set up websites and send out messages tricking people into sharing credentials or sensitive information. While the technique of using emails or bogus websites can take aim at practically anyone, sometimes the target audience can change for unexpected reasons.
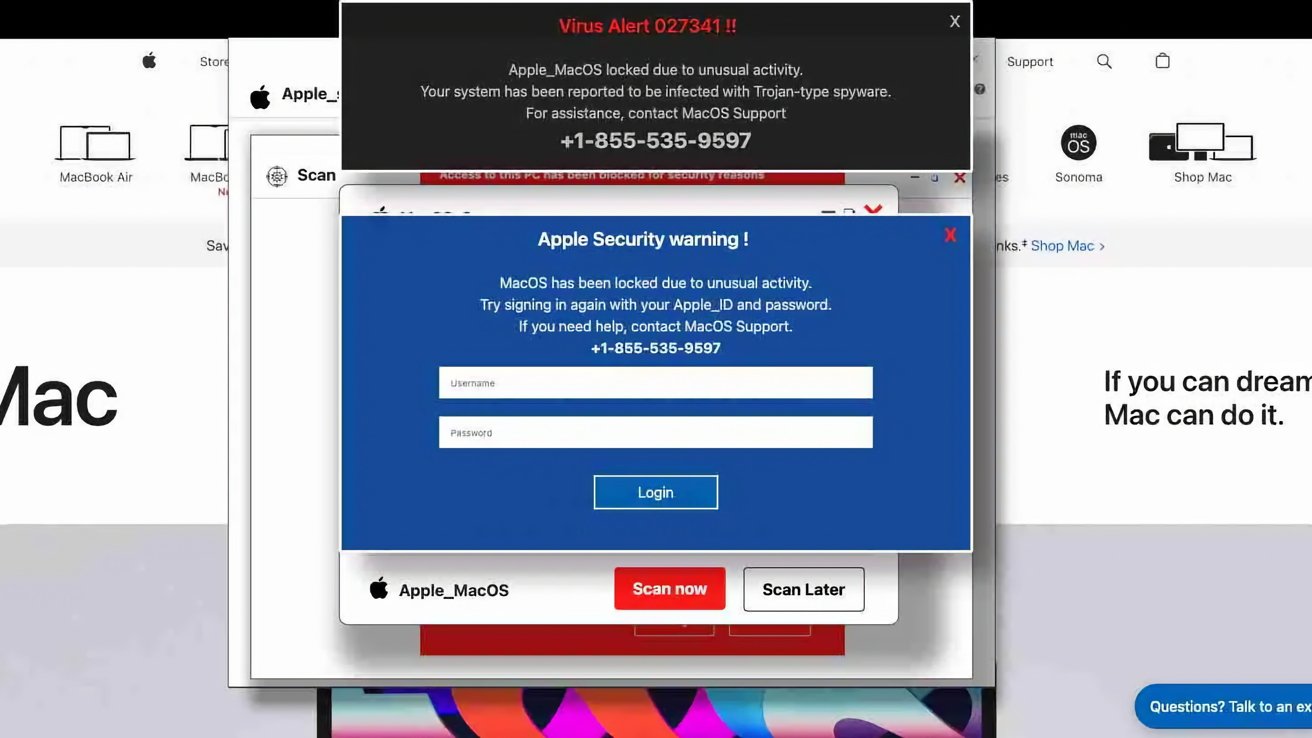
One new attack discovered by security outfit LayerX Labs has been found to target Mac users specifically. However, while the attack’s latest targets use macOS, the phishing campaign actually had a different audience at the start.
It originally went after Windows users.
Big phish
The campaign, detailed on March 19 by LayerX, was a sophisticated one that appeared to be fake security alerts within Windows. Monitored for over a year, the attack used compromised websites to display the fake warnings, claiming the PC was “compromised” and “locked.”
A window appeared, prompting users to enter their Windows username and password. At the same time, the webpage that users originally loaded up was frozen and nonfunctional due to the use of malicious code, giving the appearance of a locked screen.
Further adding to the believability, the campaign was hosted on Microsoft’s Windows.net platform, meant for hosting Azure applications, making users believe the messages were genuinely from Microsoft itself.
It was a difficult campaign to stop for other reasons too, such as the use of a hosting service for some of the page’s infrastructure that was trusted by secure web gateways and email security tools. The attackers also relied on randomized and quickly changing subdomains, which allowed the campaign to continue even if some subdomains were flagged as malicious.
The attack functioned when the victim attempted to go to a legitimate website, but accidentally included a common typo in the URL. They would be taken to a compromised domain parking page, which redirects the browser through multiple websites before hitting the actual phishing attack page.
The actual webpages and imagery used to fool users was also of a high standard, with LayerX calling them well-designed and professional in nature. There was also the use of anti-bot and Captcha verification systems, used to thwart automated tools that could detect phishing campaigns.
Bad switchers
By late 2024 and early 2025, LayerX spotted that the campaign was becoming more intensive, but it wasn’t the only one to spot it. Microsoft itself also saw the attack, and introduced a new “anti-scareware” feature to the Edge browser, thwarting the attack.
At the same time, similar protective features were added to Google Chrome and Mozilla Firefox, which also helped to cut down the number of attacks.
After their introduction, LayerX saw a massive 90% drop in the attack against Windows users. It wasn’t completely gone, with malicious pages still in operation, but it was unable to display the fake warnings to users.
With Windows users no longer a viable target thanks to the browser updates, the attackers made a decision to refocus their efforts and infrastructure at another audience: Mac users.
Just two weeks after Microsoft brought out its Edge changes, LayerX started seeing the same attacks being made against Mac users. The company didn’t observe attacks aimed at Mac until the changes were made.
Adapted attack
The new attack took on Mac users, with Safari users a prime target for the campaign, claims LayerX.
However, rather than waste the existing work on its infrastructure, the attackers kept a lot of the details the same, changing only some elements. For example, the phishing page layout and messaging was updated to be more in keeping with macOS apps.
The code was also updated to target Safari users on macOS, by using HTTP OS and user agent parameters to filter out potential victims. Oddly, despite the work to adapt, the campaign still relied on the Windows.net infrastructure.
While security companies work to catch up and to stop this phishing campaign, LayerX offers that the existence of the Mac variant shows criminals are willing to adapt. Relatively few material changes were made to switch from attacking Windows users to Mac users.
It also demonstrates that Mac and Safari users are big enough targets for online criminals to specifically target with phishing attacks.
Protect yourself
Users can typically evade phishing attacks by having good online hygiene. Checking for signs such as generic greetings in messages, wild offers and promises, and mistakes in URLs and imagery can be clear signs that something is wrong.
In the case of a browser-based attack such as the one above that claims a computer has frozen, it is usually possible to close a frozen tab or force quit the browser altogether if it is a fake warning. It’s also not likely for Apple to ever seriously offer warnings to Mac users stemming from a Windows domain of any variety.
By taking a moment to think about warnings and similar odd messages demanding credentials or payment details, many users should be able to avoid the online traps.