Statistically speaking, your passwords probably suck. At least, that’s the implication made by one cybersecurity research team, which analyzed over 19 billion leaked passwords and found only six percent were unique.
Cybernews combed through publicly available data from 200 breaches and leaks that have happened since April 2024, looking for trends and commonalities between the revealed passwords. Just over a billion were strong enough to resist dictionary attacks. The vast remainder were weak.
(To put numbers on that: Almost 18,000,000,000 passwords were no good.)
So, who are the worst offenders? A few perennial members in the hall of password shame: password, admin, 123456. Cybernews says password and admin each were found 53 million times in the set, while 123456 clocked in at 338 million. Additionally, over 727 million passwords contain the sequence 1234, or almost four percent of their data set.
As for trends within the weak passwords, Cybernews found these to be common themes:
- Names of people (#2 most common, with eight percent chance of use in one of the passwords)
- Words with positive meanings
- Pop culture references
- Curse words
- Countries
- Cities
- U.S. states
- Food
- Popular brands
- Nature
- Animals
- Seasons
- Months
Top words from these topics include:
- love (87 million)
- sun (34 million)
- joy (6.9 million)
- mario (9.6 million)
- thor (6.2 million)
- batman (3.9 million))
- fuck (16 million)
- shit (6.5 million)
- bitch (3.2 million)
- rome (13 million)
- lion (9.8 million)
- summer (3.8 million)
- monday (0.8 million)
- may (28 million)
- april (5.2 million)
- tea (36 million)
- apple (10.7 million)
- google (25.9 million)
- facebook (18.7 million)
- kia (12.7 million)
- boss (10 million)
- hunter (6.6 million)
- soccer (4 million)
- football (3.4 million)
- carolina (1.9 million)
- dakota (1.2 million)
- texas (1.1 million)
- god (24 million)
- hell (20 million)
If you’re wondering what makes for a weak password, the answer is pretty simple. It’s anything easily guessed—by either humans or computers. And these days, password-cracking software has been fed dictionaries and info on widespread habits (like replacing letters with numbers or punctuation), making those apps much more efficient at their task.

Shutterstock
Among the set of unique passwords, a few commonalities emerged, too. For length, the most popular was eight to 10 characters, with 11 characters trailing in a close 4th place. Currently, eight characters is the usual required minimum. At least 12 characters is considered the baseline for better security.
Besides password length, composition also made many of these unique passwords vulnerable to cracking. Almost one-third of these unique passwords (27 percent) used only lowercase letters and numbers. Another 20 percent combined mixed-case letters and digits but lacked special characters.
These formats, while better than lowercase letters alone, can still be brute-force attacked by a computer—where it keeps trying different combinations of characters to guess your password. When your password is shorter and has less variety in character types, the easier it’ll fall to this kind of cracking method.
So what’s the takeaway from these findings? Well, first and foremost, passkeys look even better against this backdrop. This newer alternate method of logging in requires no memorization, is resistant to cracking and also phishing, and requires no typing or copy/paste. If you haven’t begun using passkeys, you should. They’re a huge upgrade over passwords.
Can’t use passkeys? Then you should do these four things:
1. Avoid easily recognized words and phrases in your passwords.
2. Use unique passwords at least 12 characters long with upper + lowercase letters, numbers, and special characters. Ideally, the longer the better, since computing hardware continues to get faster. The chart below gives an example of how fast AI could crack passwords in 2023—which was already two years ago.
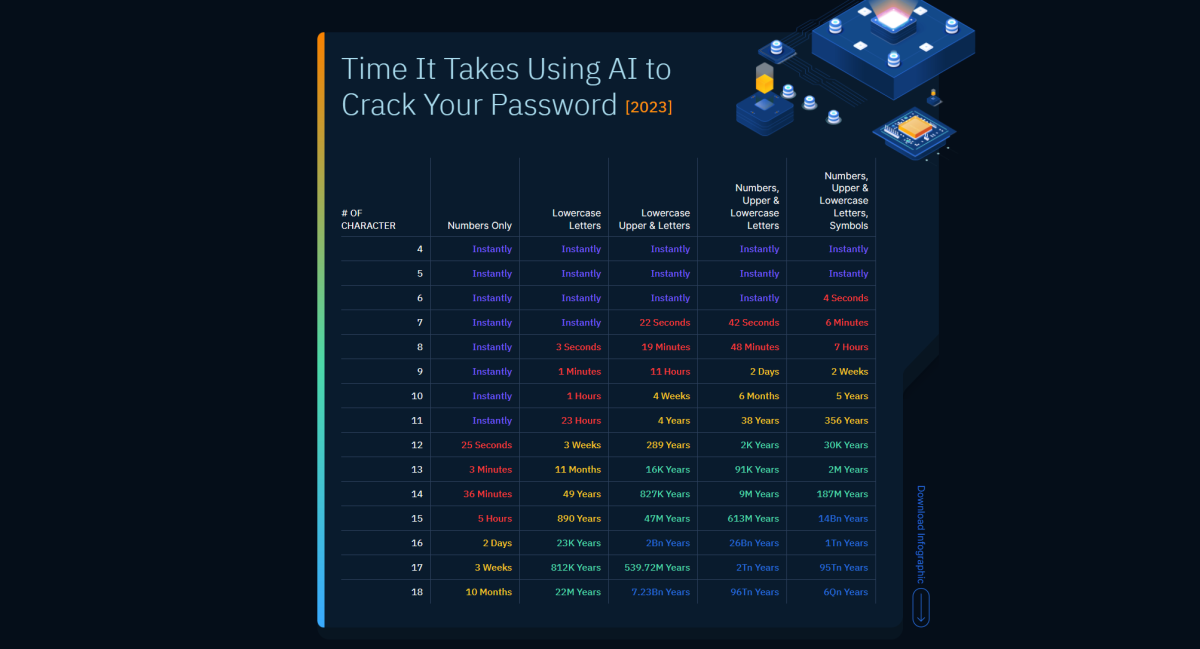
Home Security Heroes
3. Use a password manager. It’s unrealistic to memorize dozens, if not hundreds, of passwords. A password manager takes that work off your plate, and then you can make your logins much more complicated (aka stronger). The bank says you can use up to 50 characters for your password. Sure, why not?
4. Enable software-based two-factor authentication (2FA) wherever you can. Ideally, use a separate app like Bitwarden Authenticator or Google Authenticator to generate your one-time codes. Text-message-based 2FA is also an option, but it isn’t as secure. If you use it, set up a PIN on your cell phone account for number porting, and secure the account with a strong password and 2FA to lessen the risk of account takeovers and SIM jacking attacks.
Better password security sounds like a drag, but it doesn’t have to be. Start with your most important accounts first, then work your way outward. Eventually, your days of “password123456” will be far behind you.




