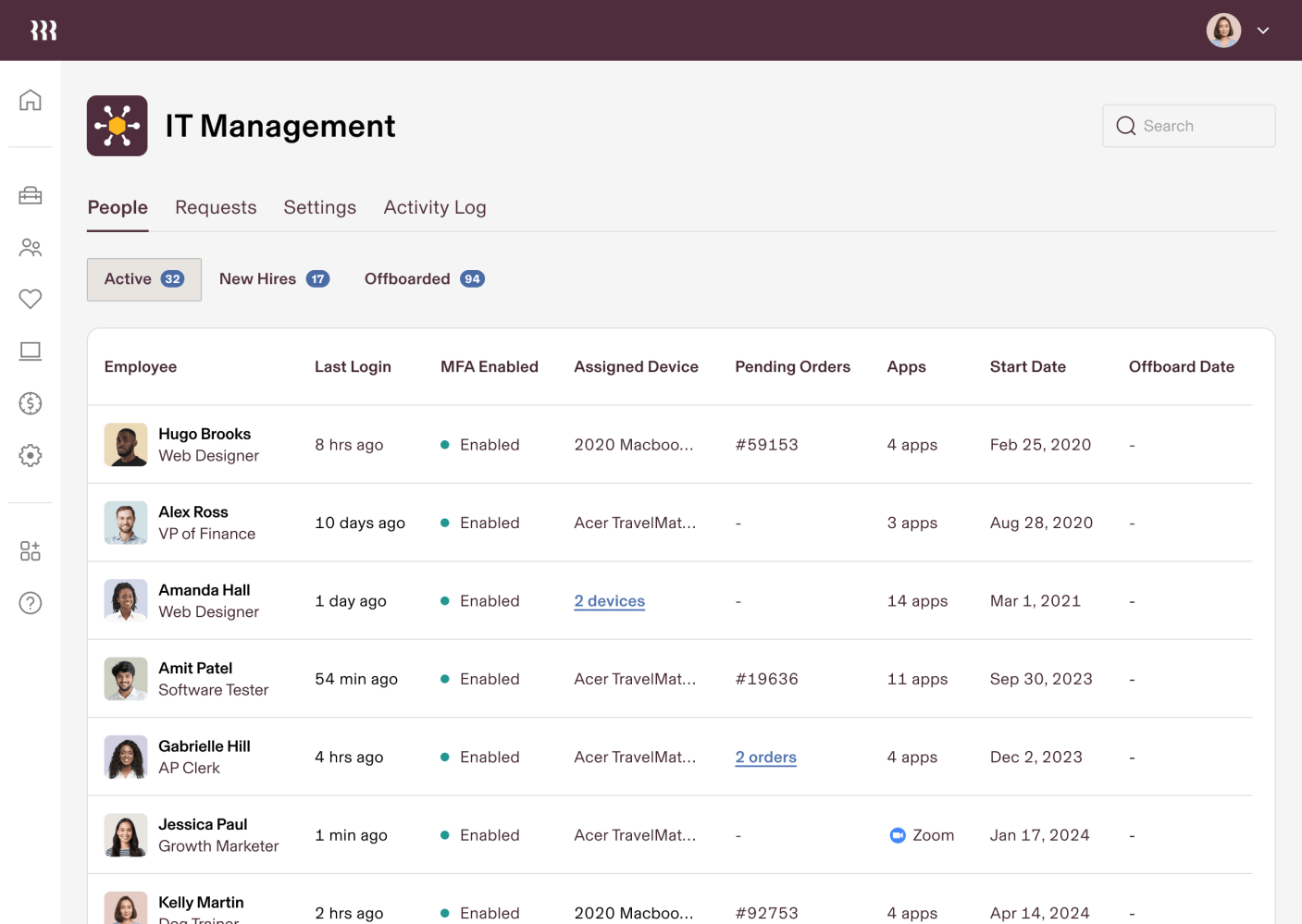
If you’re an IT admin, you’ve got a lot on your plate. Managing the entire user lifecycle can feel like a complex laundry list of manual tasks: switching between systems, provisioning access, configuring and retrieving laptops, resetting passwords, and enforcing security policies.
Chances are, you’ve tried to automate this manual work with IT solutions on the market today. But individual point solutions only solve one piece of the puzzle: whether it’s Okta for IAM, Kandji to manage Mac devices, or Intune for Windows MDM.
This leaves you stuck managing multiple disjointed systems, which severely limits how much you can truly automate, not to mention the higher software spend from using 4+ tools to successfully manage IT.
With Rippling IT, you can combine robust identity, access, device, and inventory management all in one platform. This makes it much easier to strengthen security while eliminating busywork. Here’s how:
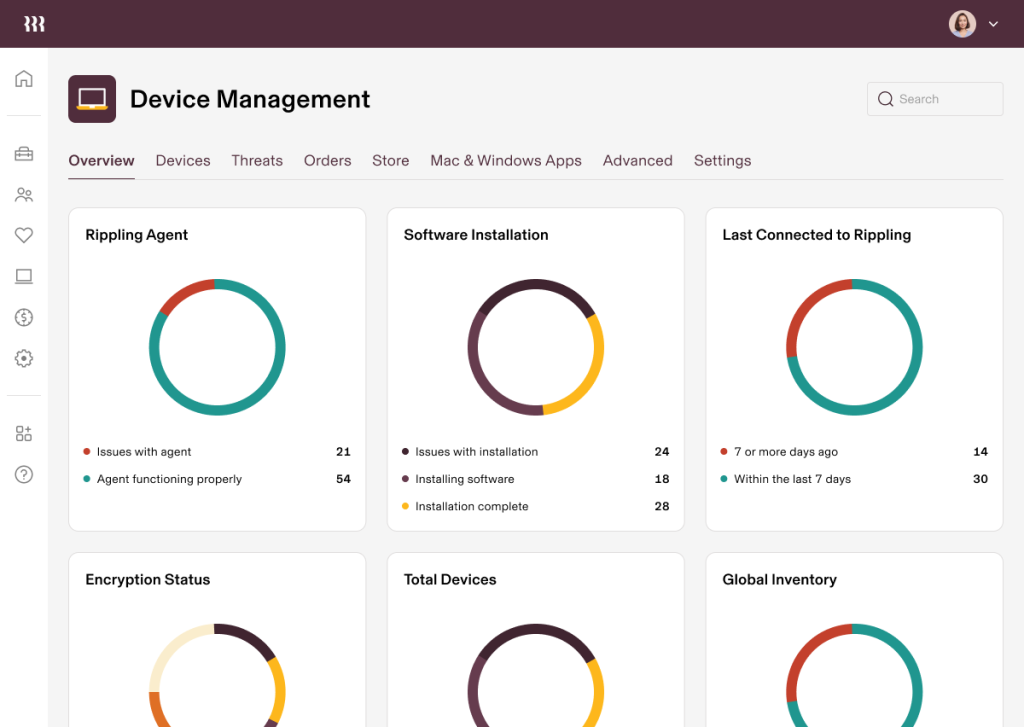
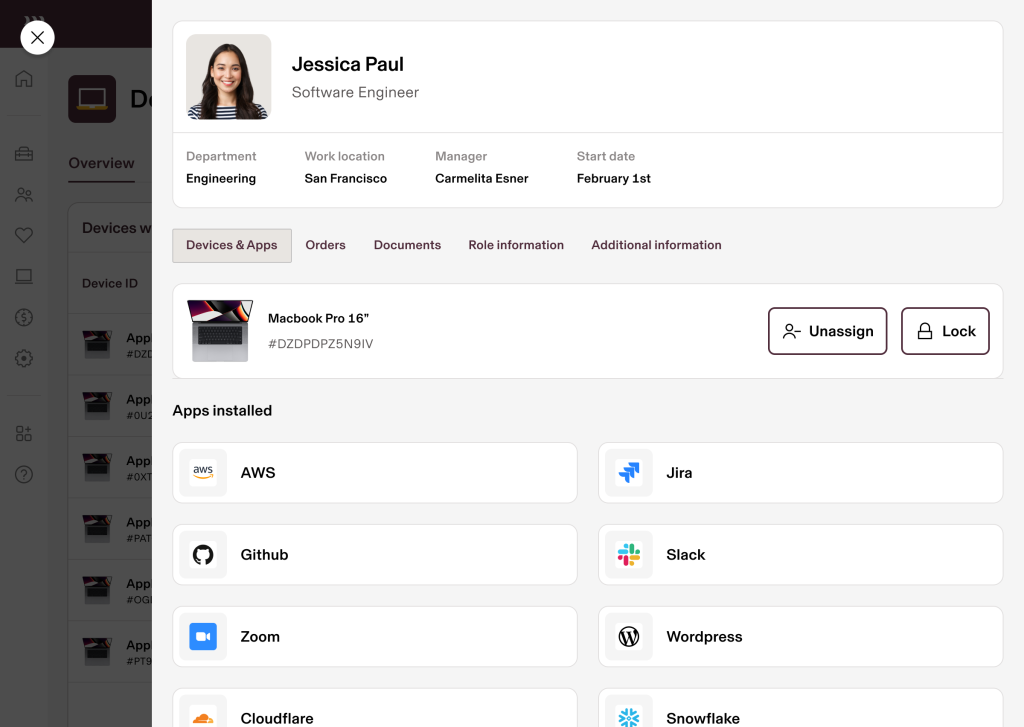
A single pane of glass (we actually mean it). Because Rippling has natively built identity and access management (IAM) alongside cross-OS mobile device management, you get holistic visibility into your security posture from one system – like what device a user has been assigned, what apps they can access (and their group membership within those apps), whether or not antivirus has been installed, and so much more.
This makes it significantly easier to enforce security controls across the user lifecycle and ensure nothing slips through the cracks. Say goodbye to fragmentation, and hello to a streamlined, consistent IT experience.
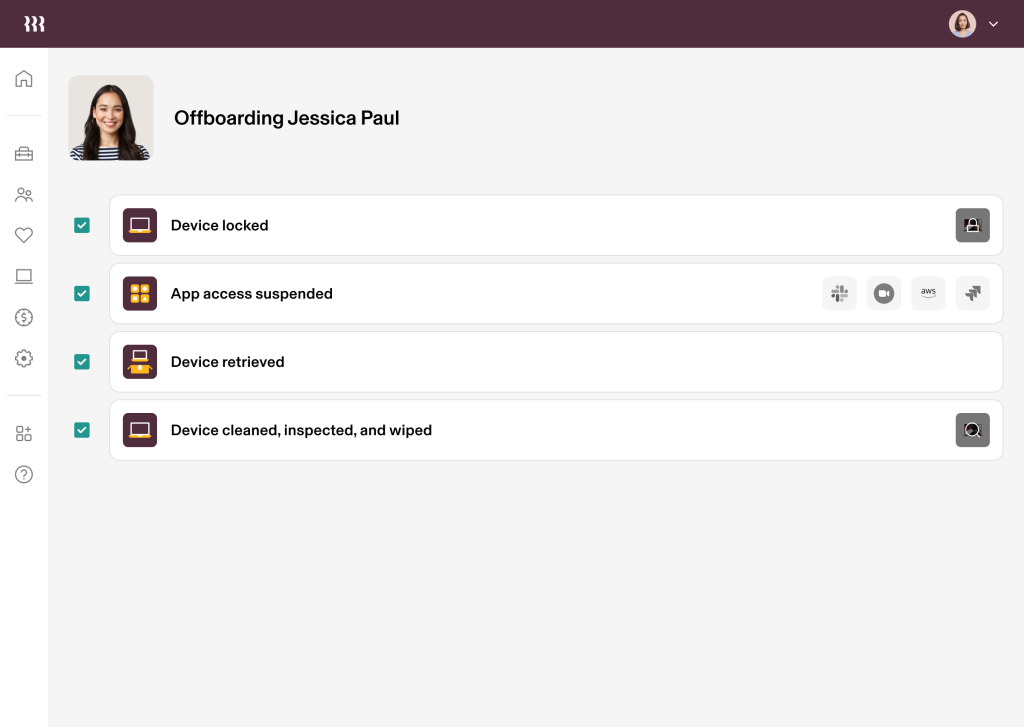
Granular, automated control. In just a few clicks, replace manual and error-prone processes with custom policies, workflows, reports, and approval chains built on device and user data. Leverage attributes like role, department, and location to target security controls at a much more granular level. For example, you could tailor authentication requirements based on access to sensitive data by requiring users in the engineering department to have a stricter MFA and password requirement than users in the sales department.
You can also easily automate key user lifecycle moments. Consider offboarding, for example. Offboarding employees can be a time-consuming process with a lot of security risks, requiring multiple systems to deprovision accounts and lock and wipe devices. That’s not even counting the trips to FedEx to physically retrieve laptops and the late nights wondering if you missed a step. With Rippling IT, you can handle all of that, automatically, from a single workflow.
Zero-touch deployment. Automatically configure laptops with the right software, access, and security settings for each user’s role. Rippling makes it simple to implement additional security measures like device trust and endpoint protection.
You can use Rippling to automatically deploy SentinelOne on all managed machines, keeping them secure with best-in-class endpoint protection. With this integration, you’re able to view threats in Rippling by employee, department, or location, and take action directly in Rippling.
Rippling offers a comprehensive solution to unify all things IT. Consolidating MDM, IAM, inventory management, password management, and endpoint security into one system is a win-win. Not only does it make your job easier and your company more secure, it also reduces costs and helps employees do their jobs better. Rippling IT empowers teams like yours to strengthen security and eliminate busywork for good.
Schedule your 30-minute live tour of Rippling IT.
Check out Rippling on Twitter/X here, and on Facebook here.
FTC: We use income earning auto affiliate links. More.




