Wireguard is a hot, modern contender in VPN protocols. Its philosophy is different, which makes it better suited for specific types of situation. Let’s take a look at what makes it unique, and what its strengths and drawbacks are.
What is Wireguard?
Wireguard is a lean, fast, and modern VPN protocol. We mentioned Wireguard briefly in our review of VPN protocols, and over the past few years, it’s gained a lot of momentum in the Linux community. It’s for good reason, too, because WireGuard takes a different approach than other VPN implementations. We’ll use OpenVPN as a point of comparison, since that’s the one most major VPN providers use under the hood.
Wireguard is less than half as old as OpenVPN’s 22 years, though it’s still proving to be fairly reliable. It’s also much leaner, at only 4,000 lines of code. That’s much easier to audit, incorporate, or build with than OpenVPN’s 70,000, and that can be critical for certain sensitive applications. Wireguard’s protocol itself also has less overhead than others, which means it uses more bandwidth on your actual data and there’s less of a tax on the system.
OpenVPN operates in user-space, which means privilege-escalation attacks aren’t likely from the program itself, but it hurts your overall throughput. Wireguard has a user-space application that’s very fast, but it also has kernel support. It’s significantly faster overall, both in theory and in practice, making it ideal for transferring large files quickly or streaming video from a personal media server.
Wireguard’s security philosophy is also different. OpenVPN is flexible, so if there’s a mismatch between the client and server, there are options and the connection can still be established. However, the cost of this approach is that there are more potential security holes, and there’s much more upkeep required by system administrators to mitigate that risk.
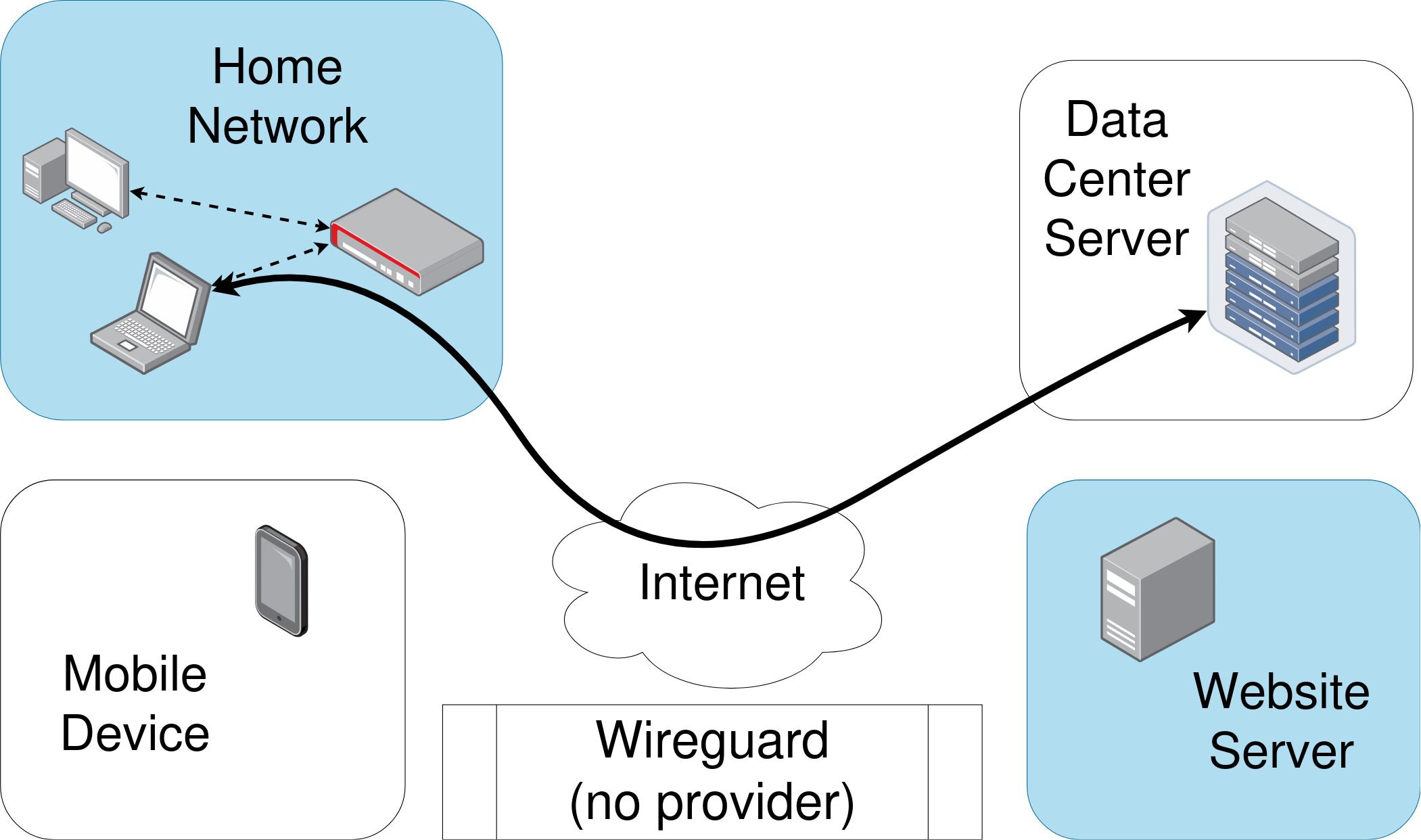
Wireguard makes a direct connection between computers, or nodes, in its own network.
Wireguard is built to be less flexible—each version is based around specific algorithms and processes. If there’s a mismatch between two devices in the network, they will not connect. This means that system administrators mainly just need to make sure things are updated regularly. There’s a variety of other differences between Wireguard’s implementation and traditional VPNs as well. There’s a lot of depth once you start to get more technical.
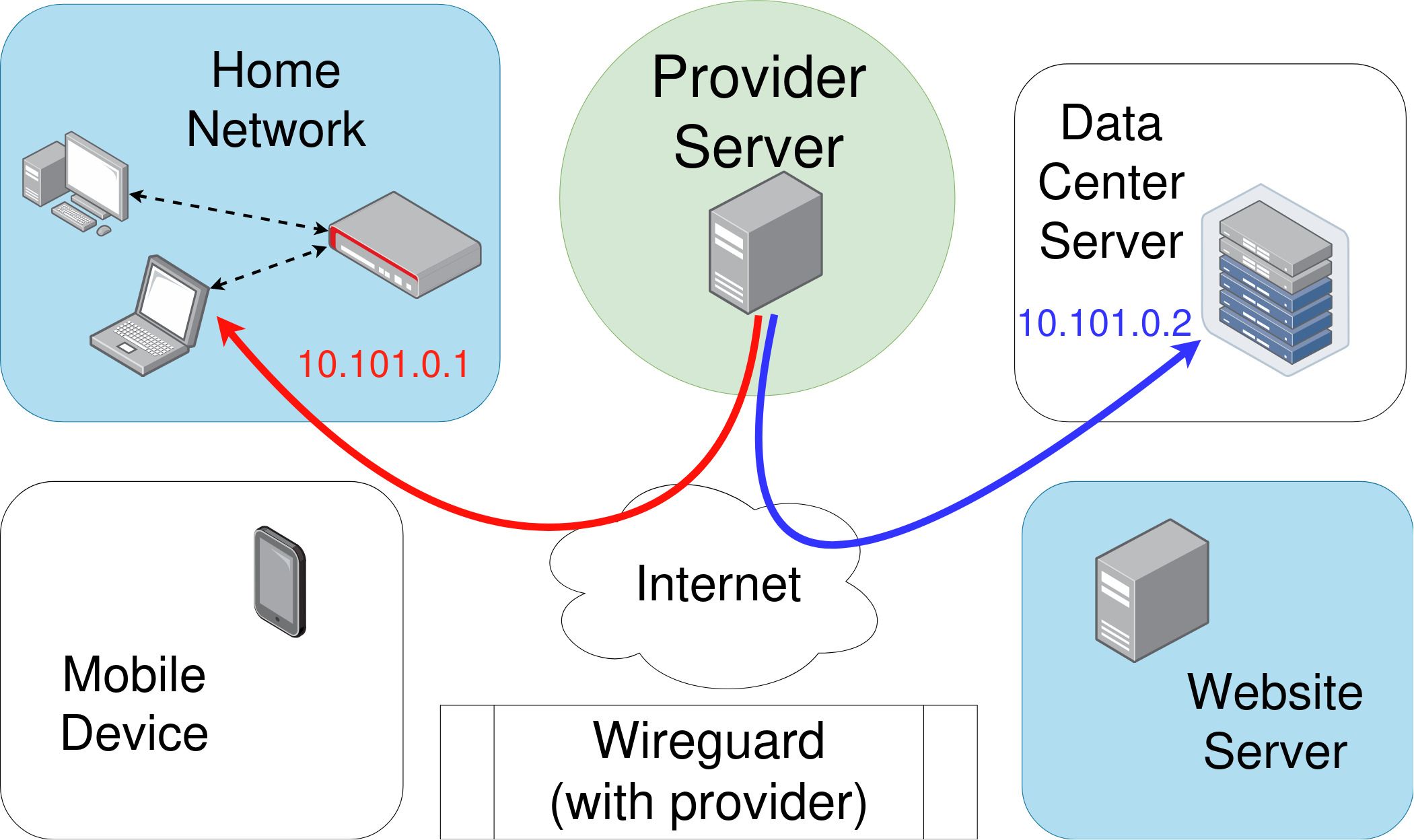
It’s important to mention here that while you can use Wireguard directly, you can also use a Wireguard provider to help you set up and organize your connections.
A Wireguard provider configuring and assigning IP addresses to two nodes.
What Can I Use Wireguard For?
Wireguard has a variety of use cases that are fairly different from traditional VPNs. While you can use Wireguard to route your web traffic through a different server, its strengths are actually well suited to different tasks.
Wireguard shines when you want to create a direct internal network between different computers in different places. Each computer—or node—basically creates its own connection and route to every other computer in your Wireguard network. It doesn’t rely on routing traffic through a central server when used this way. This is what we call a mesh network. Think of mesh wireless networks, but for the layout of your nodes.
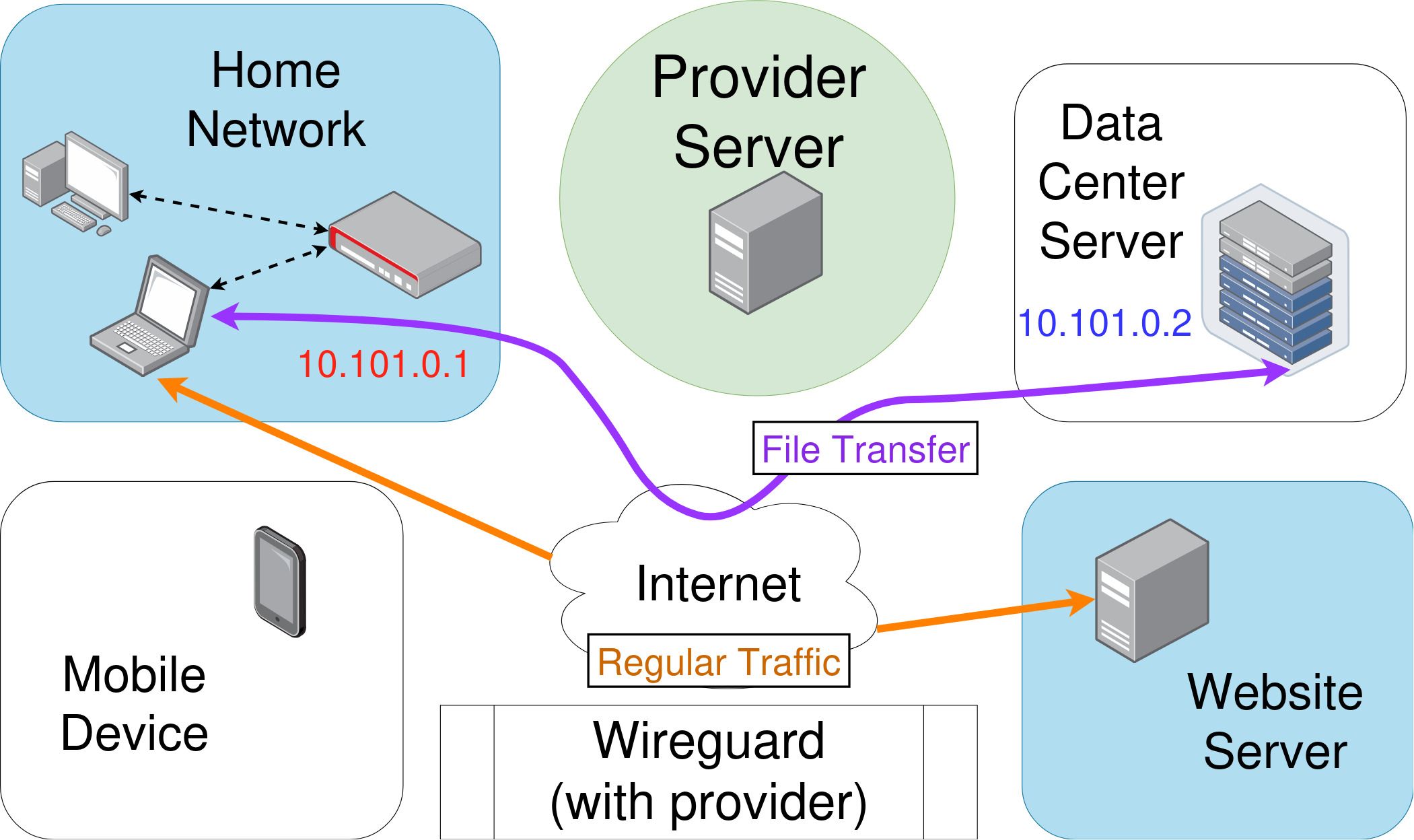
Most Wireguard providers also default to a “split-tunneling” type of configuration. This means your regular traffic of Youtube videos, Spotify, and web browsing still uses your main internet connection, which is more direct and faster than going through any kind of VPN. However, when you want to send a file to another node, it automatically goes through the Wireguard connection you made. Traditional VPN servers and clients both need to be configured specifically to allow this.
YouTube traffic can be sent over your regular connection, while you can still send a file securely to your Wireguard node at high speed.
One other aspect that’s worth mentioning is that Wireguard also works well with spotty connections. OpenVPN and other older protocols don’t always do well when the connection isn’t stable. If you connect from mobile devices or a laptop, when you might often disconnect and reconnect or roam on the network, they may not reconnect properly. Or, they can drop data. Wireguard tends to work much more reliably in these situations.
Because of these aspects, Wireguard works well when you want to share internal services—like a backup service, a video library, or a game server. The other nodes can be in many different places, on different devices, and can still function normally outside their private communication with each other. A few great applications are:
- Developers who work with cloud servers and can now access them as if they’re on site
- Friends who want to game together but can’t access their router to forward ports
- A family sharing a home backup or media server with a college student in their dorm
- Developers sharing internal resources amongst each other while their project is ongoing
- Self-hosting enthusiasts who want to share private resources between multiple servers across providers
- Regular folks who want to stream high quality video
If you use a VPN Provider that uses Wireguard, you may also be able to use it to stream video from major content providers, just like an OpenVPN-based service, but with significantly better speeds.
Does Wireguard Have Any Disadvantages?
Despite its strengths, Wireguard also has a few big drawbacks which will limit when you want to use it. These are complexity and privacy concerns which differ from those you find with traditional VPN services.
Many folks use Wireguard for a different type of network than OpenVPN: to connect individual nodes together directly to form their own network. Working with Wireguard directly can be a pain. For each node you add to your network, you have to share its key with all of the others that you want it to communicate with. Generating these configurations might be a little complex for beginners.
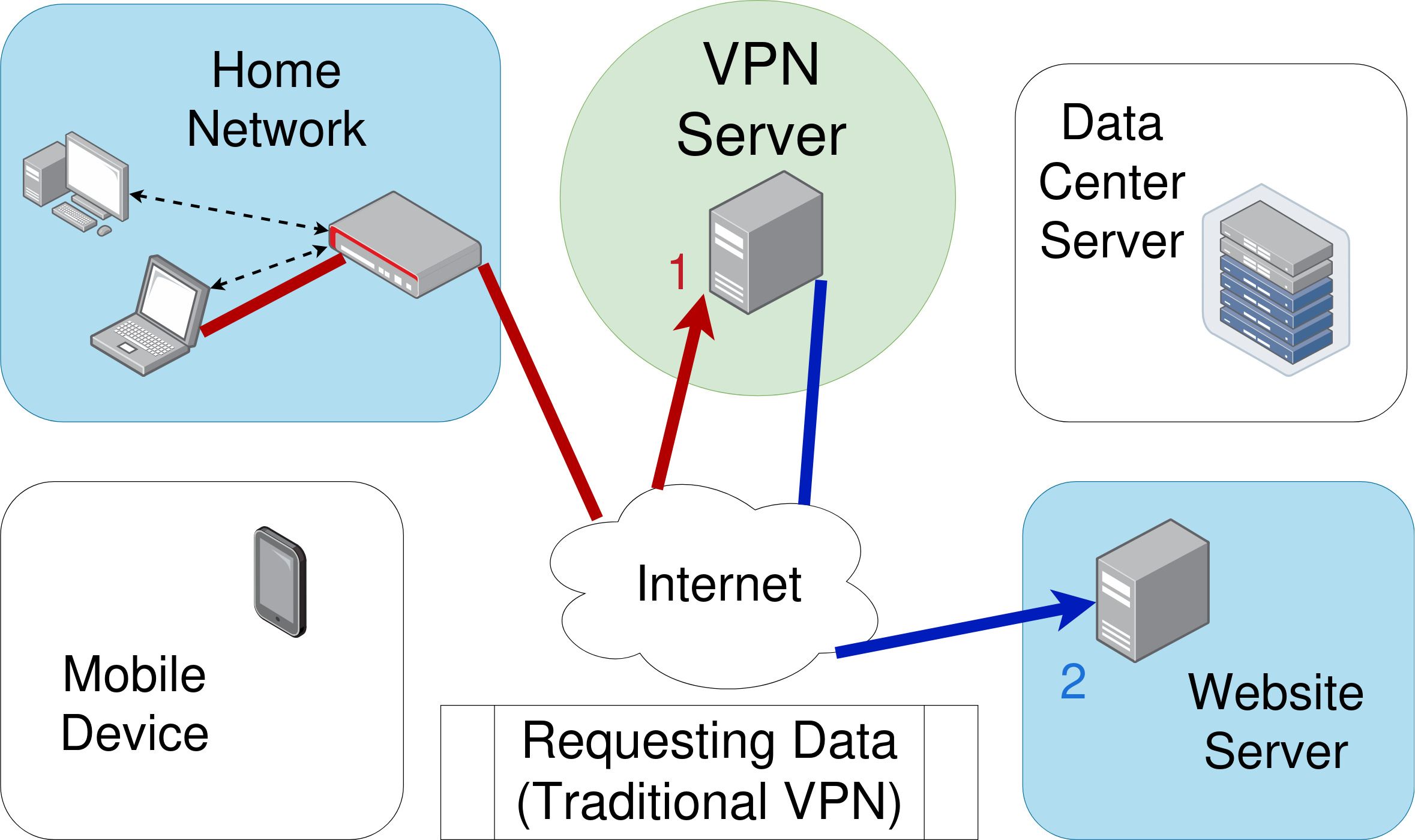
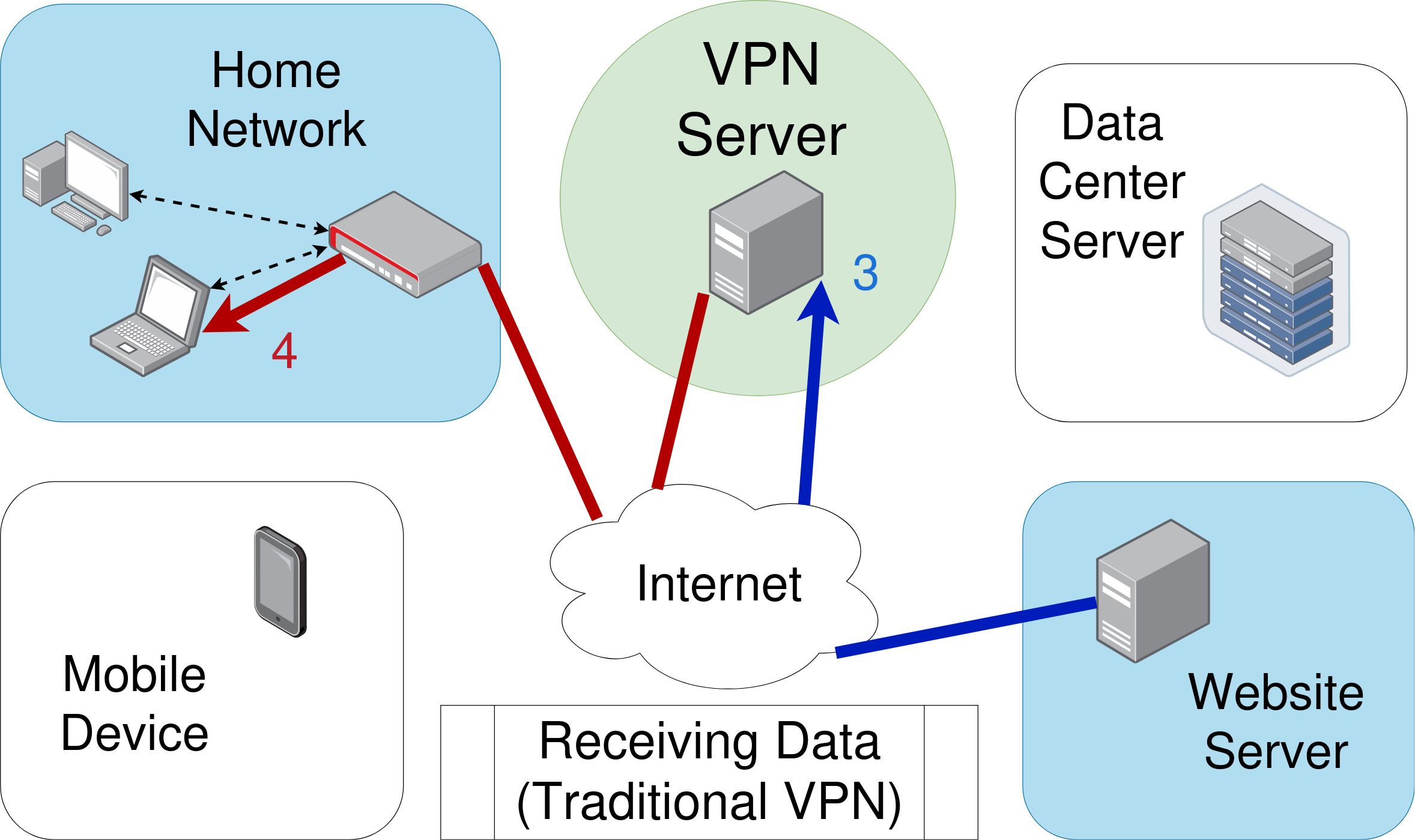
OpenVPN server requests data on your behalf from a website.
You can configure a Wireguard server and use it like a regular VPN provider as well. That can get complicated quickly and you probably will prefer a traditional VPN service.
Wireguard is also easier to block than OpenVPN-based services. If you’re in a place where your well-being depends on your internet security, Wireguard is not a good solution for you.
OpenVPN server relays that website’s response data back to the original client.
As mentioned, there are Wireguard providers you can use—free and paid services available which are built on top of Wireguard that add a level of convenience. For example, Netmaker makes it easy to add and remove nodes, as well as add DNS entries for each. Nebula adds support for user and device management, as well as for access controls. Tailscale is designed to work from user-space, has a very approachable interface, and is fairly popular in the self-hosting community. Popularity and adoption mean that you have more tutorials and people to ask when you run into issues.
You can use these providers to make your life easier, but in exchange, you give up some level privacy. Traditional VPNs can also be a privacy concern, specifically regarding logging of IP addresses, but there isn’t anything inherent to the protocol that requires storing that information. Wireguard stores the IP address information in order to operate. This is usually temporary, but the fact remains that it’s a potential risk. Some providers allow you to self-host the servers, but that’s niche and doesn’t guarantee you can use all the features they offer, either. Contrast that with the convenience of home routers that have OpenVPN servers built in, or the great apps many traditional providers offer.
Should You Use Wireguard?
Wireguard is a fast and efficient alternative to traditional VPN services. It has better performance and a different model of security and connections, making it a better fit for some specific but common situations. If you need to send and receive large files quickly, share access to a home backup server, or work with cloud servers as if they’re local to your network, you should look into Wireguard. This is especially true if you want split-tunnelling alongside any of those. It also works well with devices that disconnect and reconnect frequently, such as mobile devices or traveling laptops.
If complexity or maintenance concerns outweigh privacy, you can look for a VPN provider that’s built on top of Wireguard.
However, its complexity, approach to security, and questions of privacy might be deal-breakers for you. You should stick to a standard VPN service if you’re trying to route all your traffic through a server in a different place, need to get granular with access controls, have the means to host your own server, or because you trust your long-standing provider and their policies over someone new. Some VPN services are even free!
Many traditional VPN providers also offer Wireguard connections now, which means you can pick and choose which you want to use, or compare and contrast on your own to find the right tool for the right situation.