Apple lets you sync passwords via iCloud through a clever mechanism that keeps your secrets safe from all snoopers—including Apple. iCloud Keychain syncs passwords among all iPhones, iPad, and Macs associated with the same iCloud account for which Keychain is enabled in Settings > account name > iCloud (iOS/iPadOS), the iCloud preference pane (Mojave or earlier), or the Apple ID preference pane’s iCloud section (Catalina or later).
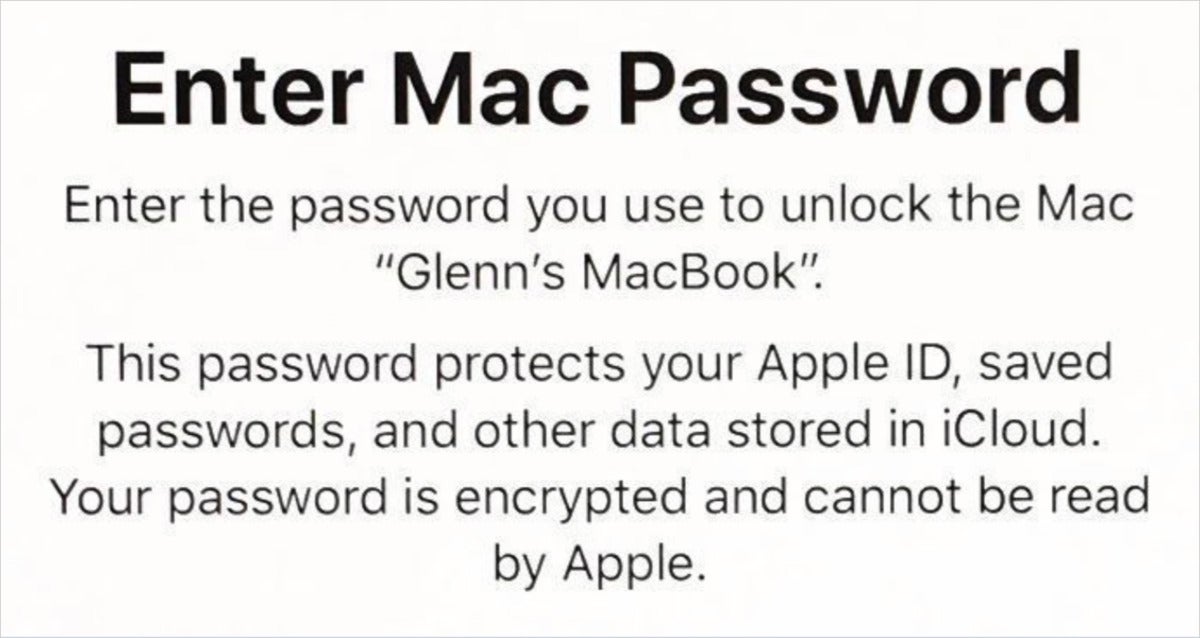
However, when you log into an iPhone, iPad, or Mac with a fresh install, on a new device, or with a new macOS account on a Mac, Apple will prompt you to enter the password or passphrase of one of your other devices. This might seem a bit like malware when you first see it—partly because you can’t find a match for the text that Apple displays on Apple’s support site—but it’s a natural consequence of how Apple protects your data securely without having access to your passwords.
 IDG
IDGWhile this message appears mysterious, it’s not insidious: it’s really part of a clever validation step for iCloud Keychain.
iCloud Keychain and a few other kinds of information—like facial recognition matches in Photos—are encrypted using keys that are stored on each device you own. While Apple operating systems generate these keys, they’re kept locally and never shared or transmitted. Apple syncs encrypted data that only you can decrypt—that’s why iCloud Keychain can’t be accessed from iCloud.com. (Technically, there are ways to do browser-side encryption that doesn’t leak the keys; 1Password and other companies offer this in their ecosystems. But given Apple’s device focus, it doesn’t make sense for it.)
With iCloud Keychain, adding a device means enrolling it as a member of a set of devices. Your first device initiates the process, and Apple may display and have you enter a security code or validate your Apple ID login for that one. It can’t confirm with other devices, because it’s the only member.
However, with your second and any subsequent devices, Apple bootstraps and daisy chains the process. It bootstraps it by using the password or passcode of an already enrolled device, like your first in the set, to encrypt the keys needed to access the set of paswords stored in iCloud Keychain. It daisy chains it by letting the security you’ve established on your first device be extended to the second, once you validate yourself.
When you’re prompted in iOS, iPadOS, or macOS to enter a passphrase or passcode from another device, Apple uses that to unlock the encryption keys needed for iCloud Keychain. Apple doesn’t have access to that device password, either: it’s encrypted on the device to which the password corresponds, and only by you entering the identical password can the contents protected by it be unlocked.
For non-cryptographically minded people, which is most people, this operation seems obscure and potentially threatening. Apple could reduce the concern by adding documentation and screen captures on its Web site.
This Mac 911 article is in response to a question submitted by Macworld reader Caroline.
Ask Mac 911
We’ve compiled a list of the questions we get asked most frequently along with answers and links to columns: read our super FAQ to see if your question is covered. If not, we’re always looking for new problems to solve! Email yours to mac911@macworld.com including screen captures as appropriate, and whether you want your full name used. Not every question will be answered, we don’t reply to email, and we cannot provide direct troubleshooting advice.




